Require SSE-S3 Encryption
Require SSE-S3 Encryption
Amazon S3 supports both server-side encryption (with 3 key management options: SSE-KMS, SSE-C, SSE-S3) and client-side encryption for data uploads. Amazon S3 provides flexible security features to prevent unauthorized users from accessing your data. You can connect to S3 resources from Amazon Virtual Private Cloud (Amazon VPC) using the VPC endpoint
In this section, we create S3 Bucket Policy to require encryption of data at rest.
-
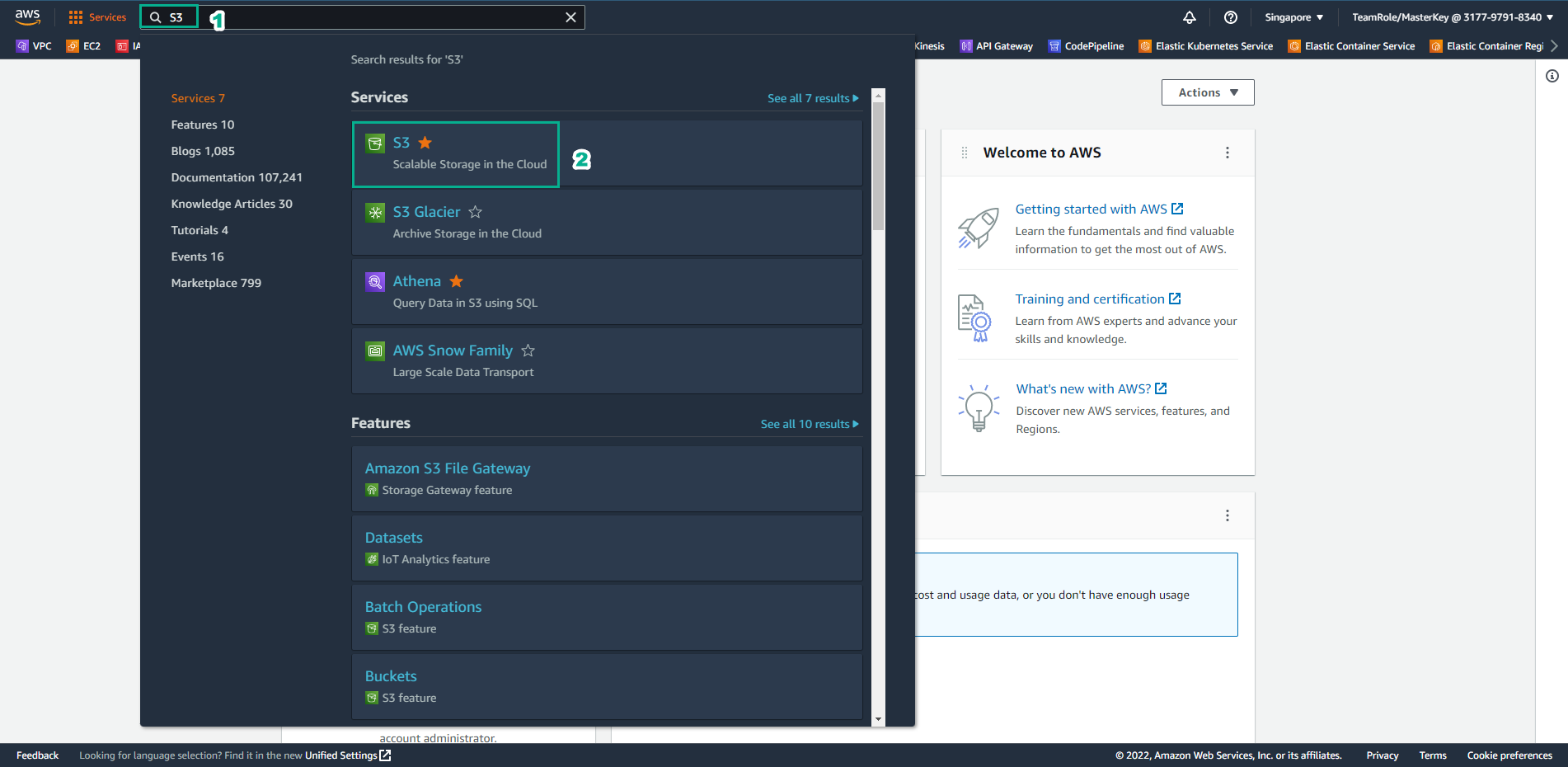
Similar to the previous lab, we access AWS Management Console
- Find S3
- Select S3
-
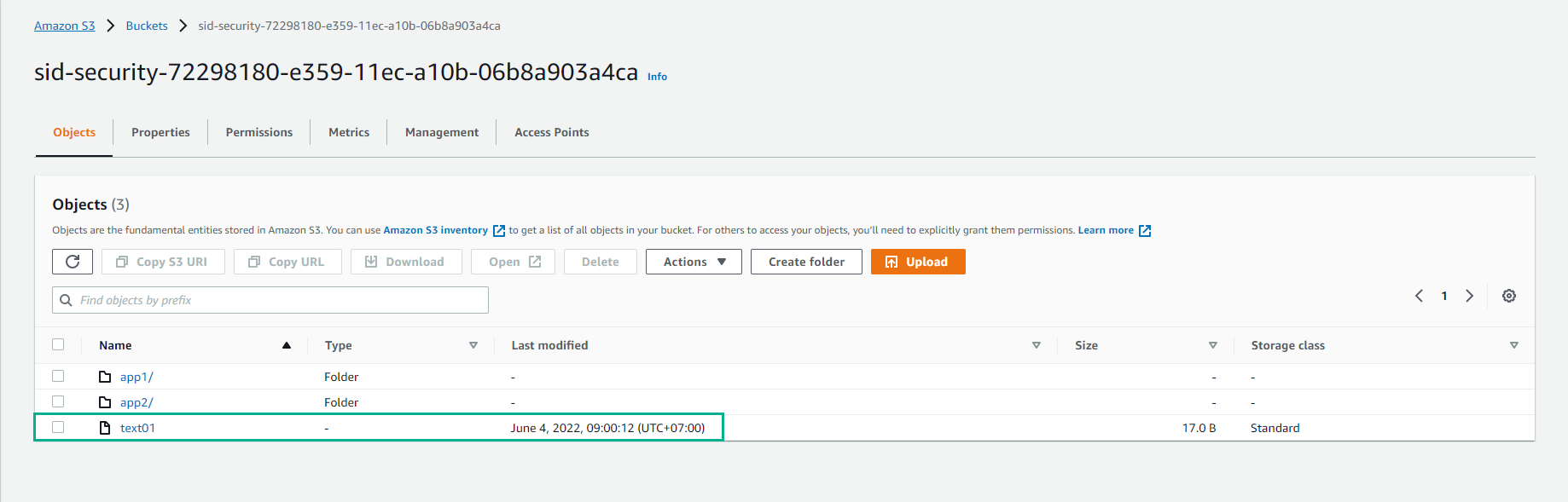
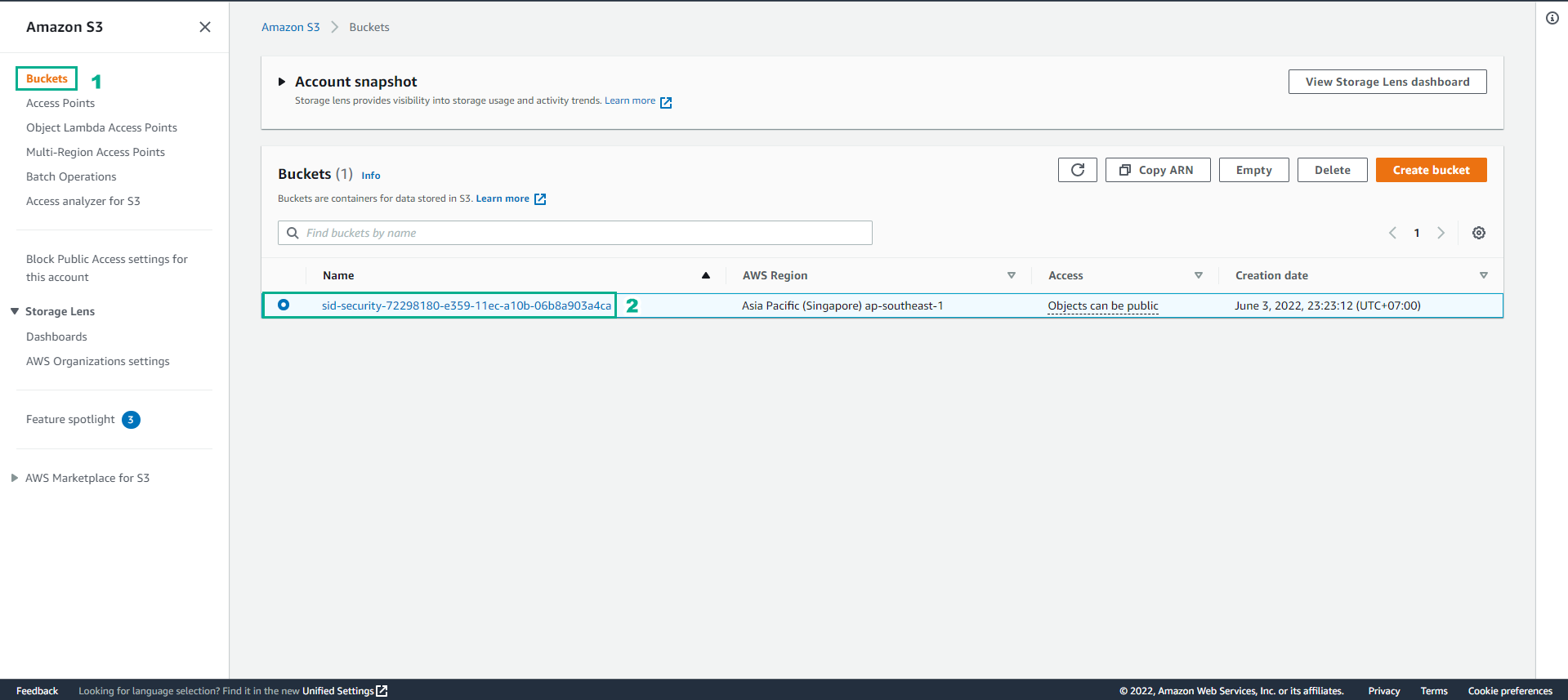
In the S3 interface
- Select Buckets
- Select sid-security-xxxxxxx bucket
-
In the sid-security-xxxxxxx bucket interface
-
Select Permission
-
In Bucket policy, select Edit
-
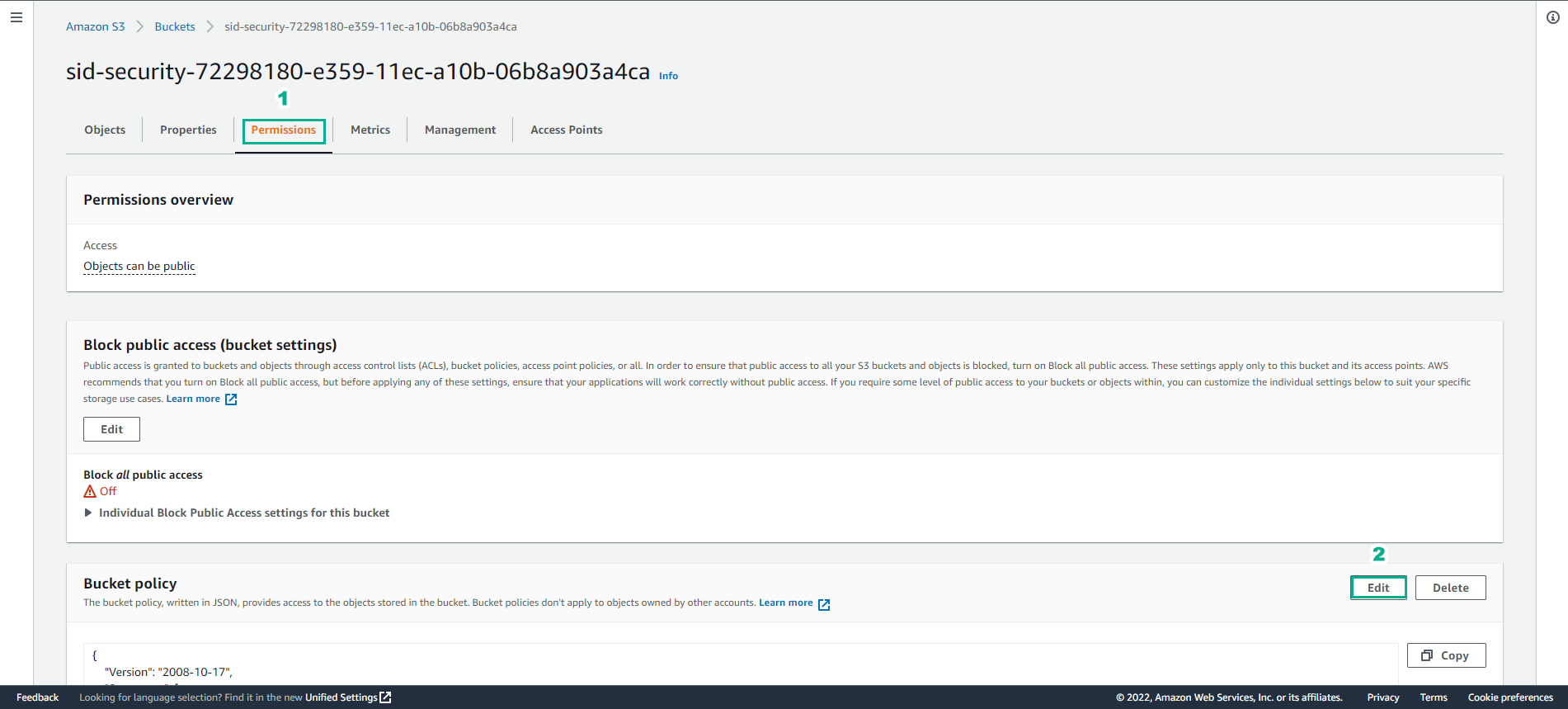
- Copy bucket policy to Bucket Policy Editor
{
"Statement": [
{
"Effect": "Deny",
"Principal": "*",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::BUCKET_NAME/*",
"Condition": {
"StringNotEquals": {
"s3:x-amz-server-side-encryption": "AES256"
}
}
}
]
}
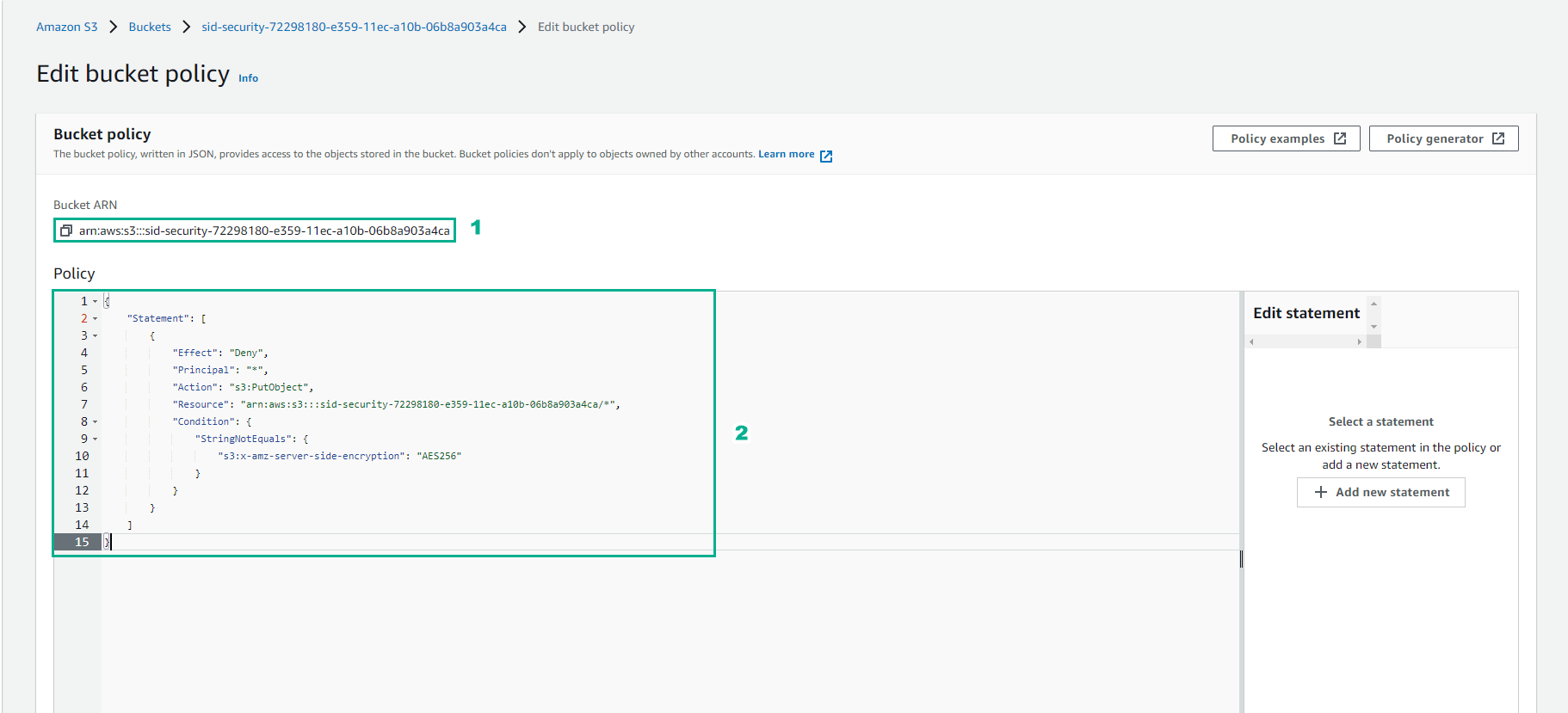
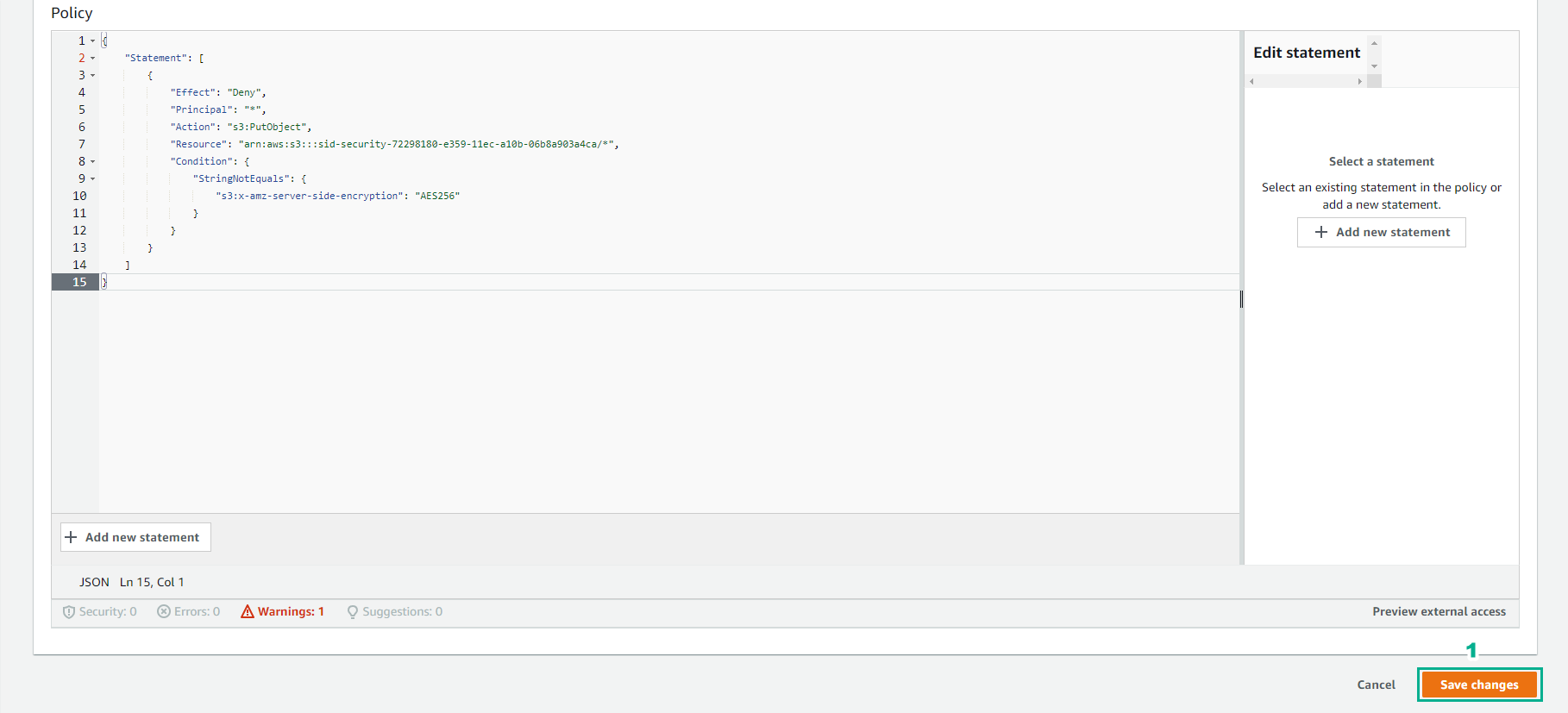
- Replace BUCKET_NAME with the bucket name you copied into your text editor and click Save changes.
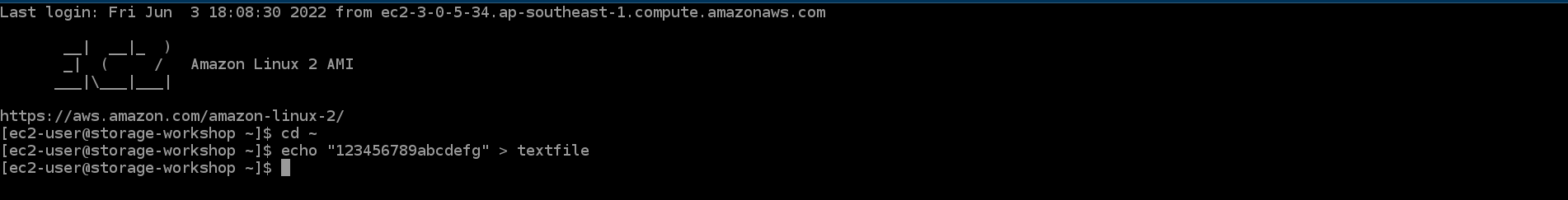
- Return to the SSH interface. Run command
cd ~
echo "123456789abcdefg" > textfile
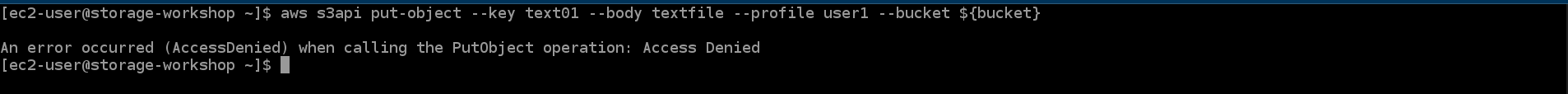
- Execute the command put an object into the bucket
aws s3api put-object --key text01 --body textfile --profile user1 --bucket ${bucket}
The request will fail because the object is not encrypted.
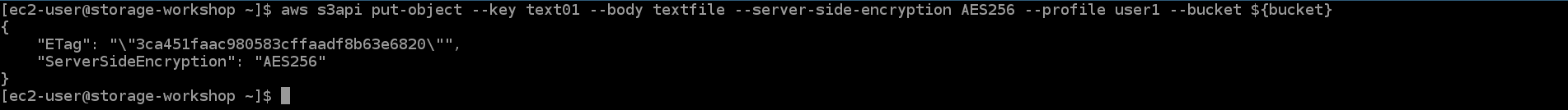
- Continue running put object using SSE-S3 encoding
aws s3api put-object --key text01 --body textfile --server-side-encryption AES256 --profile user1 --bucket ${bucket}
The command was successful because the PUT used SSE-S3.
- Check S3 has 1 file text01