Block Public ACLs
Block public ACL
-
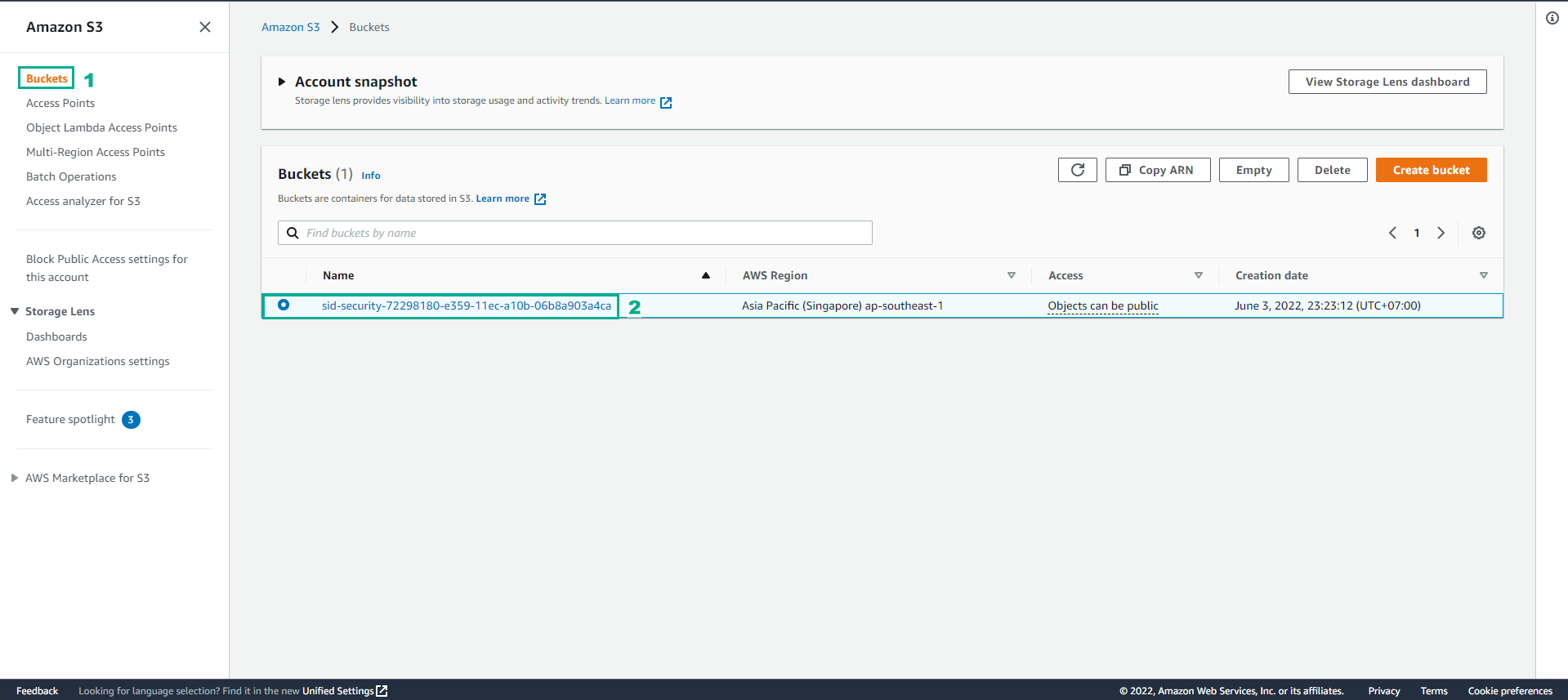
Same as before, go to Amazon S3
- Select Bucket
- Select sid-security-xxxxxxx bucket
-
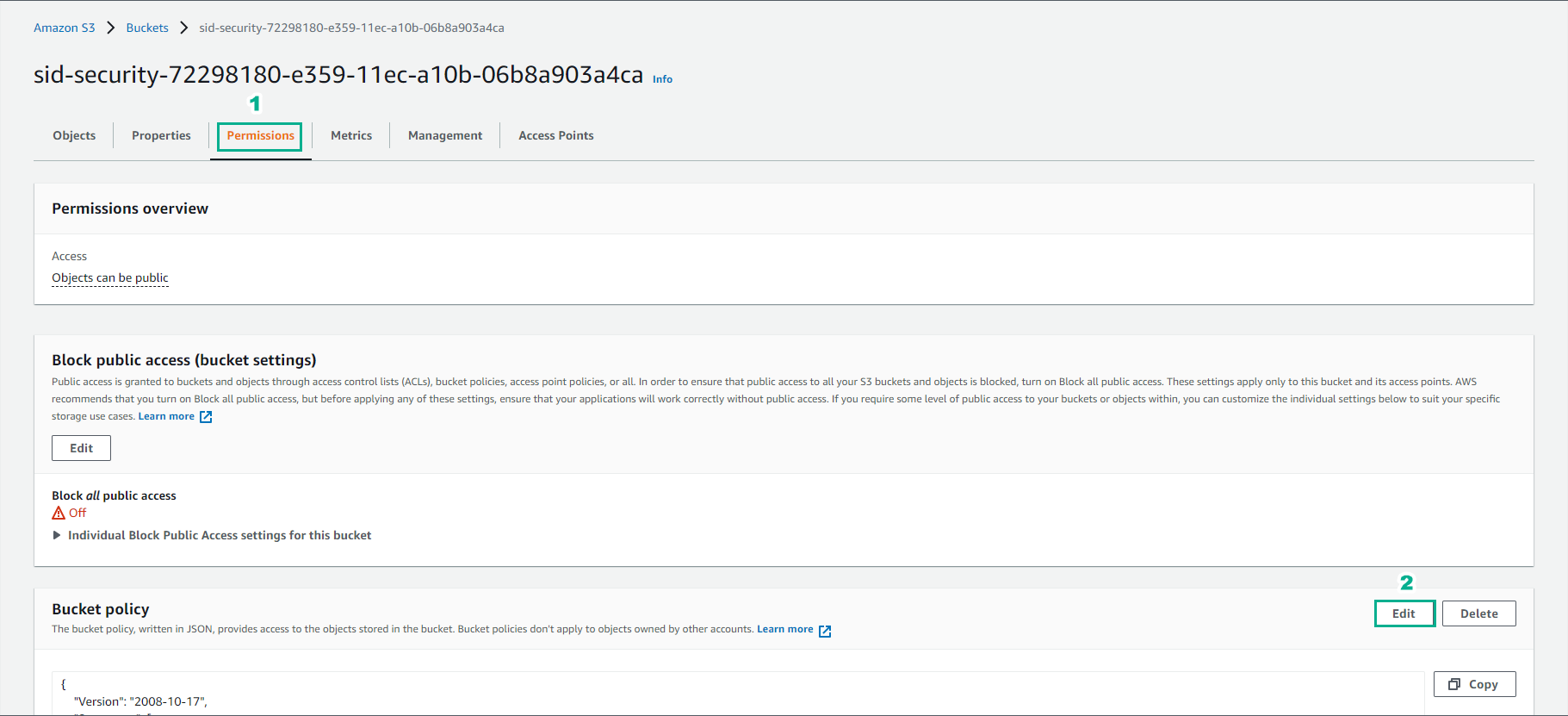
In the sid-security-xxxxxxx bucket interface
- Select Permission
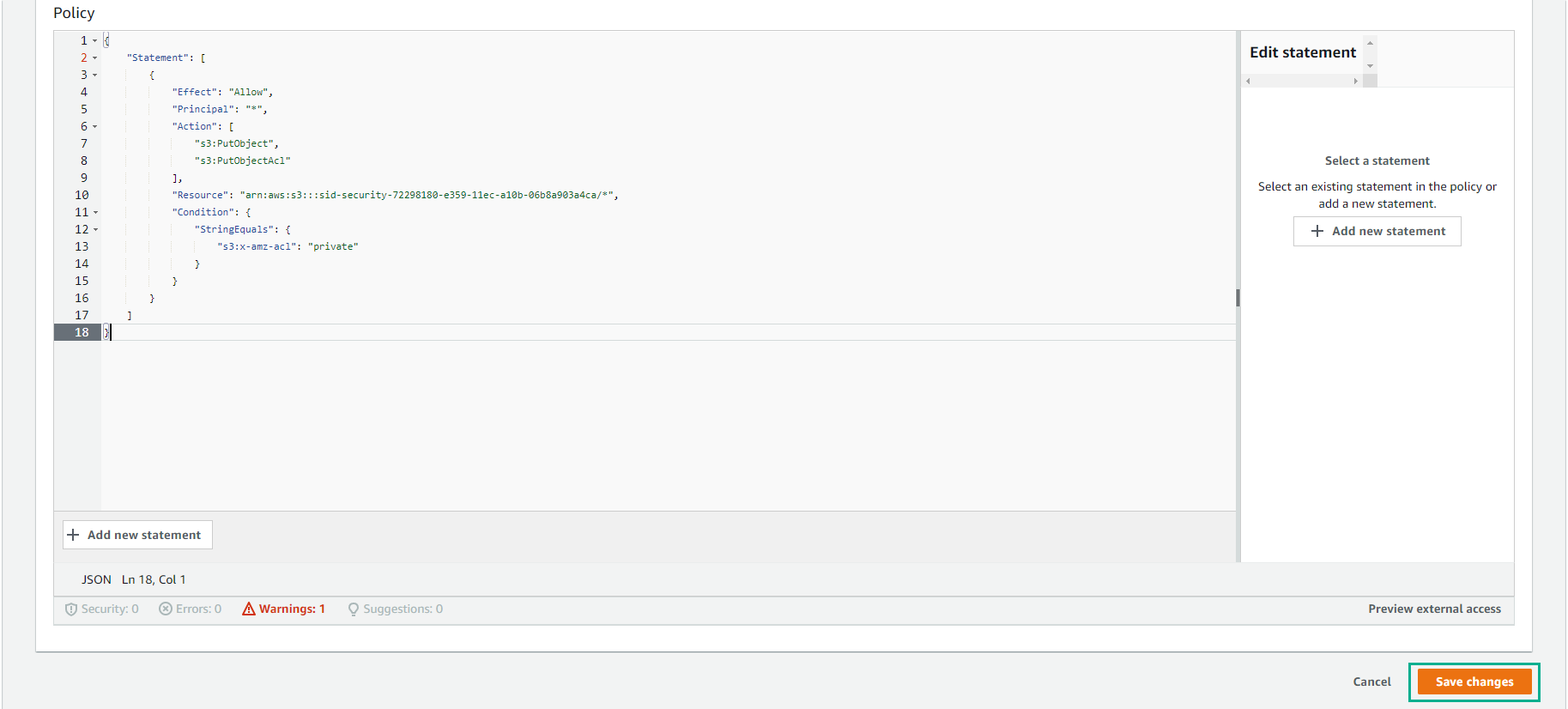
- Under Bucket Policy select Edit
- Copy the bucket policy to Bucket Policy Editor*
{
"Statement": [
{
"Effect": "Allow",
"Principal": "*",
"Action": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": "arn:aws:s3:::BUCKET_NAME/*",
"Condition": {
"StringEquals": {
"s3:x-amz-acl": "private"
}
}
}
]
}
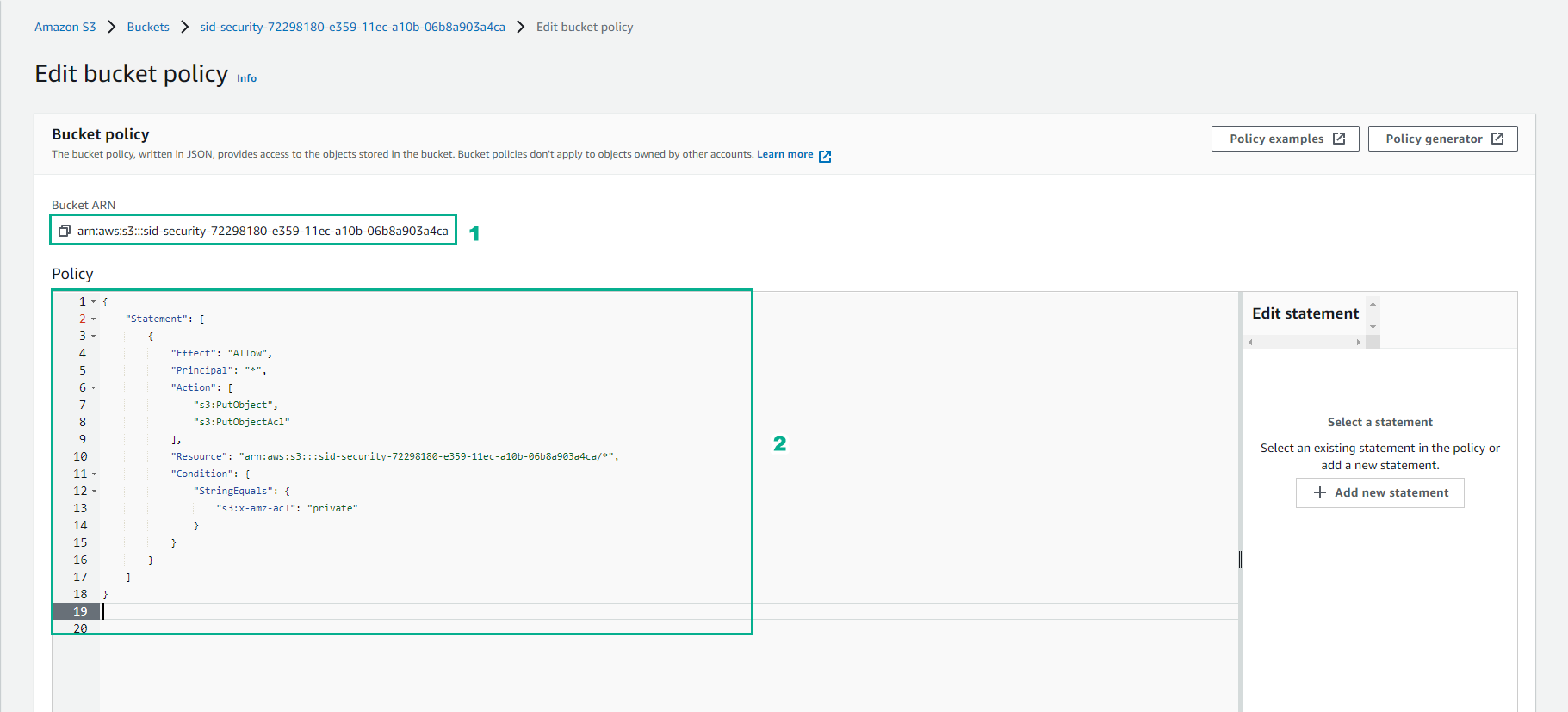
- Replace BUCKET_NAME with the bucket name you copied into your text editor and click Save changes
- Go back to the SSH section and connect to SID-security-instance
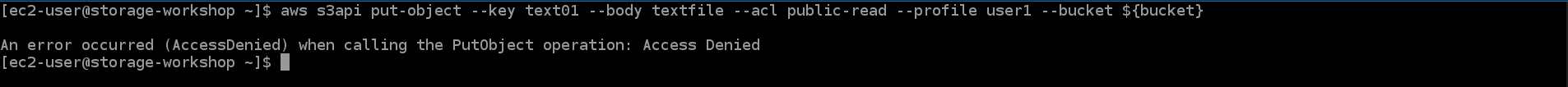
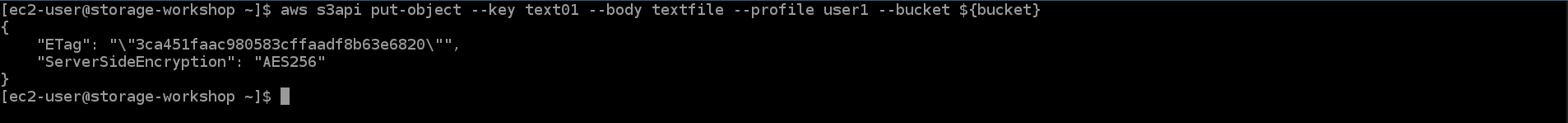
aws s3api put-object --key text01 --body textfile --profile user1 --bucket ${bucket}
The request will succeed because the default for an ACL object is private.
- Continue running the command
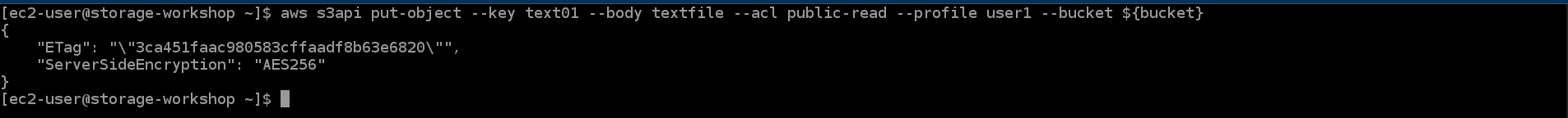
aws s3api put-object --key text01 --body textfile --acl public-read --profile user1 --bucket ${bucket}
This command also succeeds, but it is not the behavior one would expect
Current Group Policy allows private ACLs but does NOT DELETE anything. It is important to write policies that prevent actions, not allow them when trying to restrict actions against a group. The current group policy also allows Public access to unintentional groups because the main character is a wildcard.
-
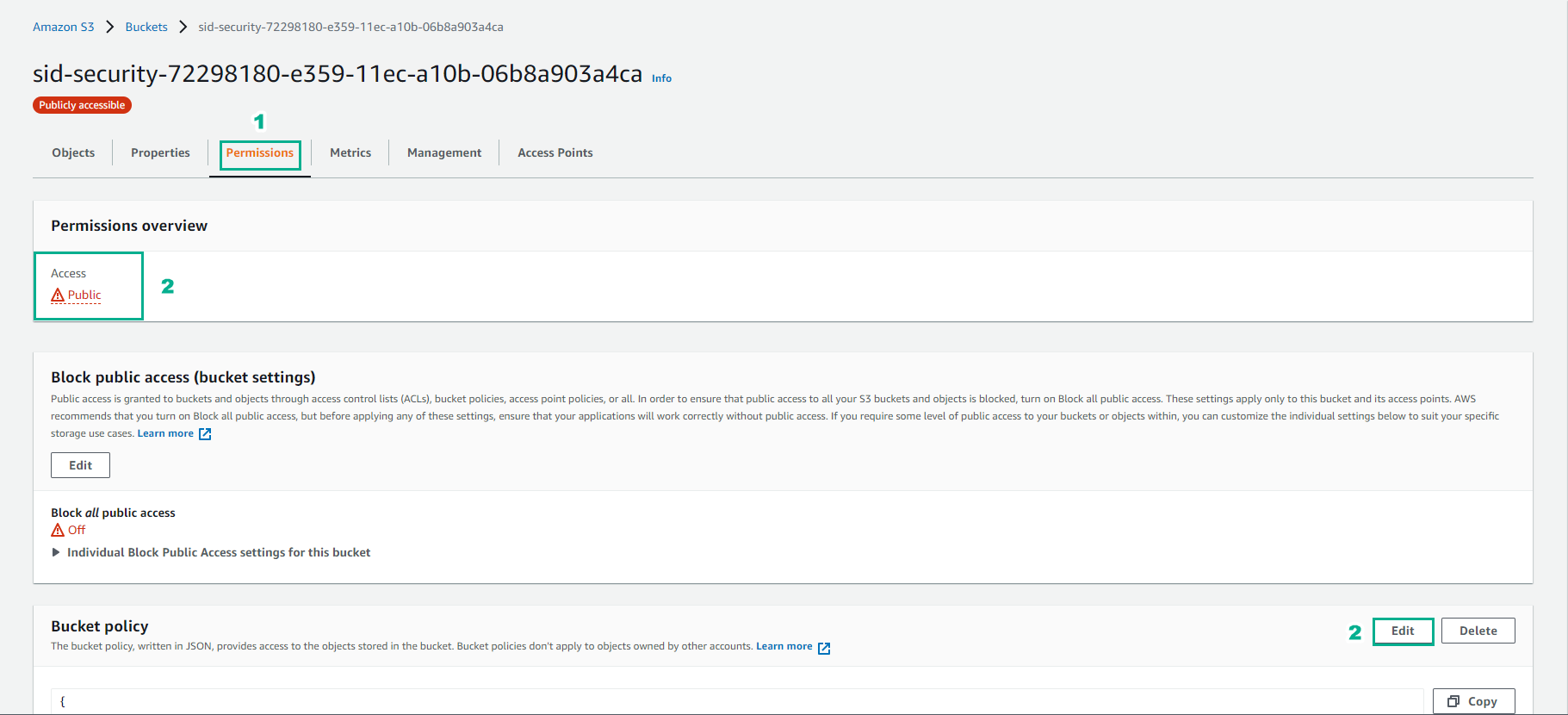
Access to S3
- Select buckets
- Select sid-security-xx bucket
- Select Permissions
- Select Edit Bucket policy
- Replace new policy
{
"Statement": [
{
"Effect": "Deny",
"Principal": "*",
"Action": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": "arn:aws:s3:::BUCKET_NAME/*",
"Condition": {
"StringEquals": {
"s3:x-amz-acl": [
"public-read",
"public-read-write",
"authenticated-read"
]
}
}
}
]
}
- Select Save changes
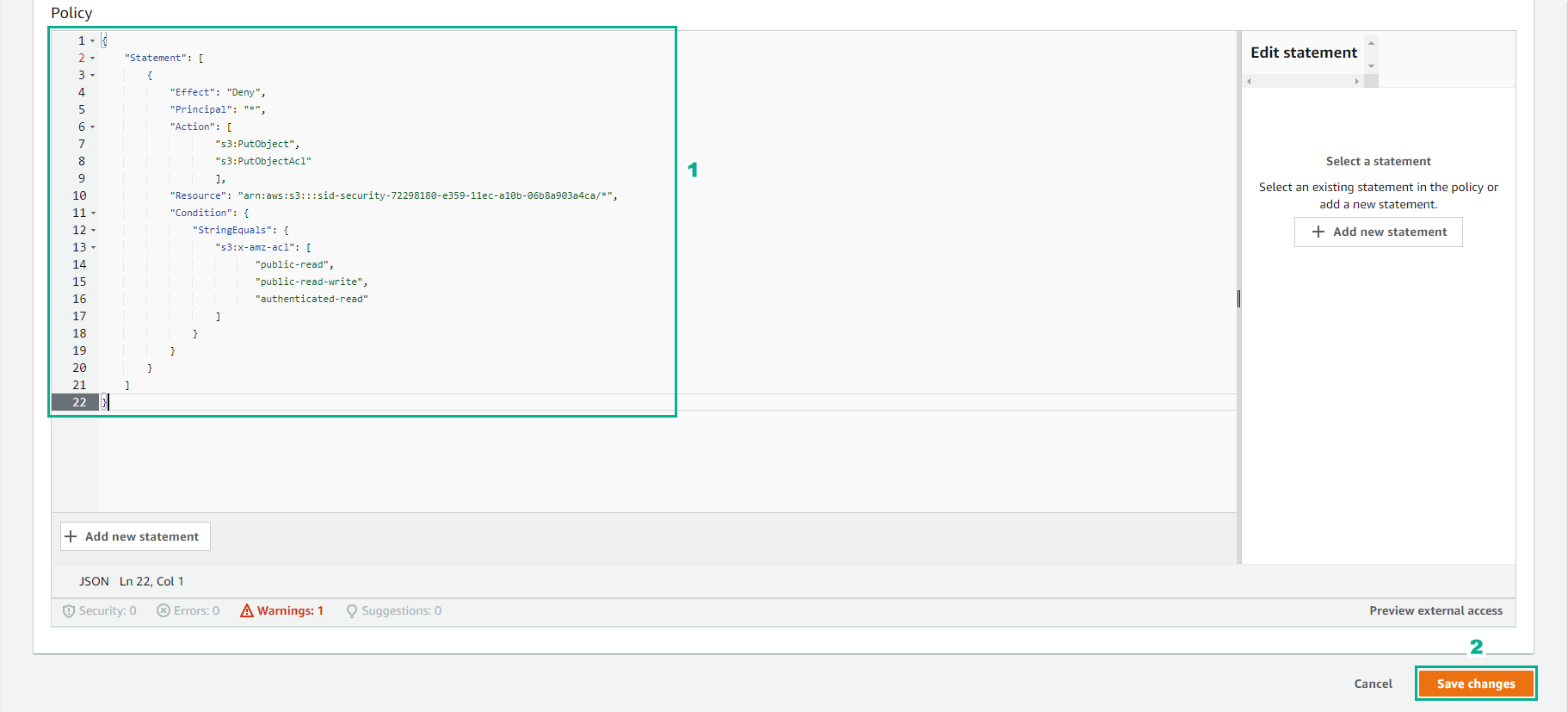
- Edit the policy successfully.
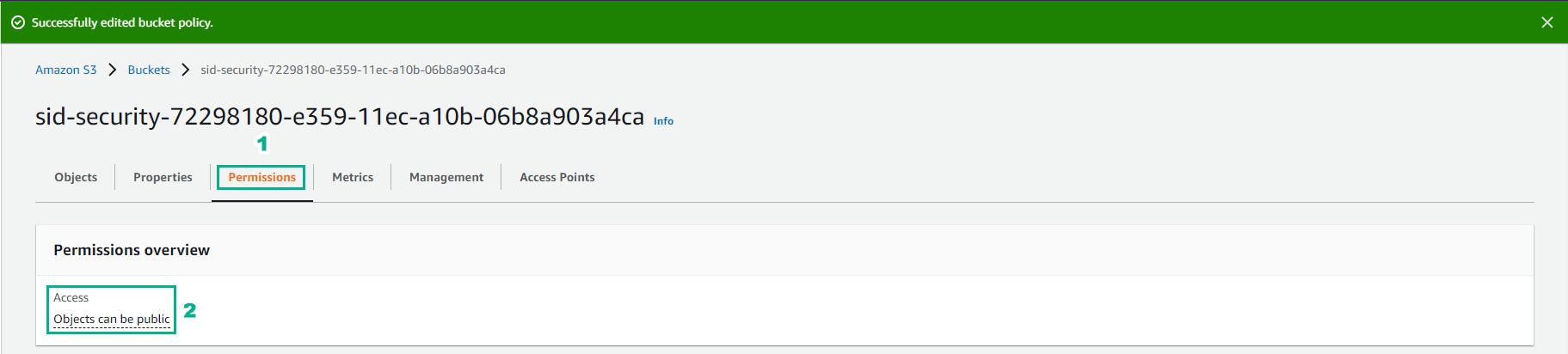
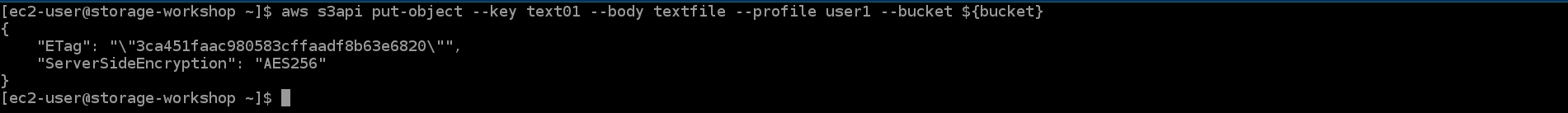
- Back to the SSH interface, run the following command.
aws s3api put-object --key text01 --body textfile --profile user1 --bucket ${bucket}
The request will succeed because the default for an ACL object is private.
- Continue to run the following command.
aws s3api put-object --key text01 --body textfile --acl public-read --profile user1 --bucket ${bucket}
The request failed because group policy now restricts the ACL from being read publicly.