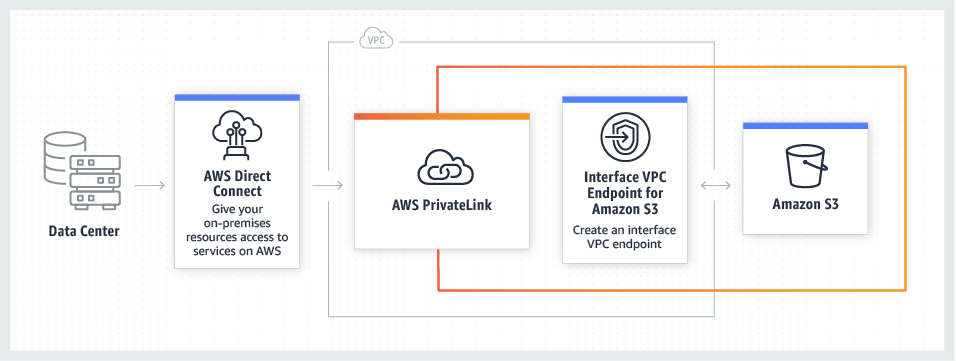
Restrict access to S3 VPC Endpoint
Restrict access to S3 VPC Endpoint
-
Access AWS Management Console
- Find VPC
- Select VPC
-
In the VPC interface
- Select Enpoints
- Select Create endpoint
-
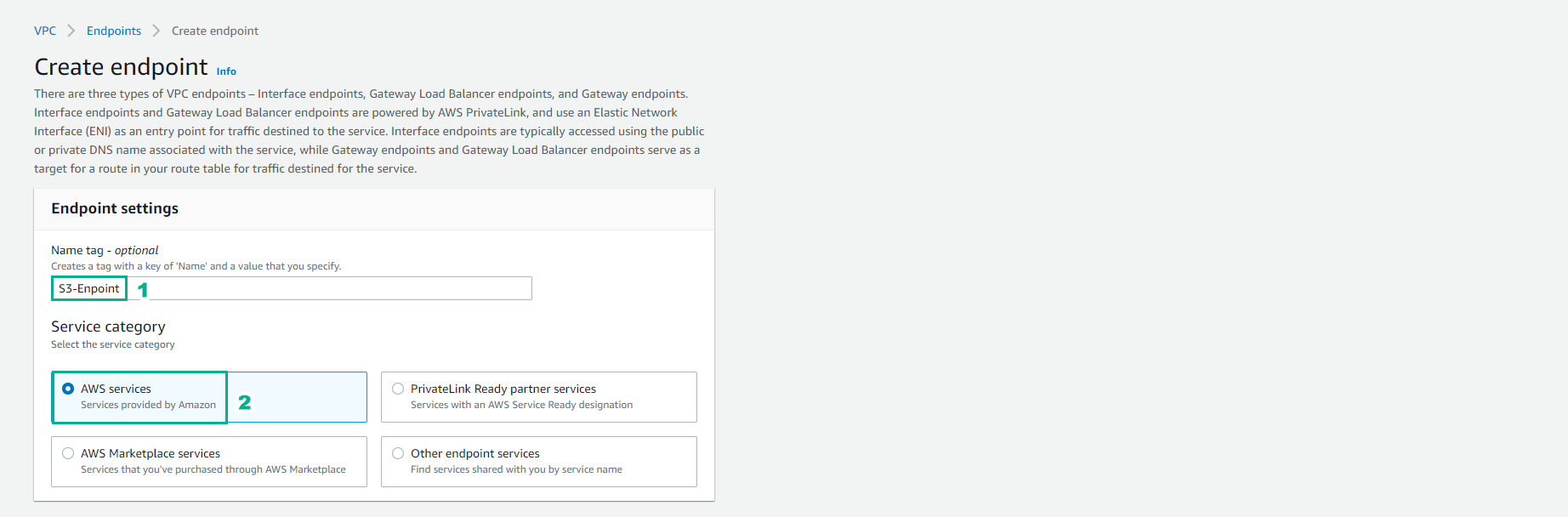
In the Create endpoint interface
- Name tag, enter
S3-Endpoint - Select AWS services
- Name tag, enter
-
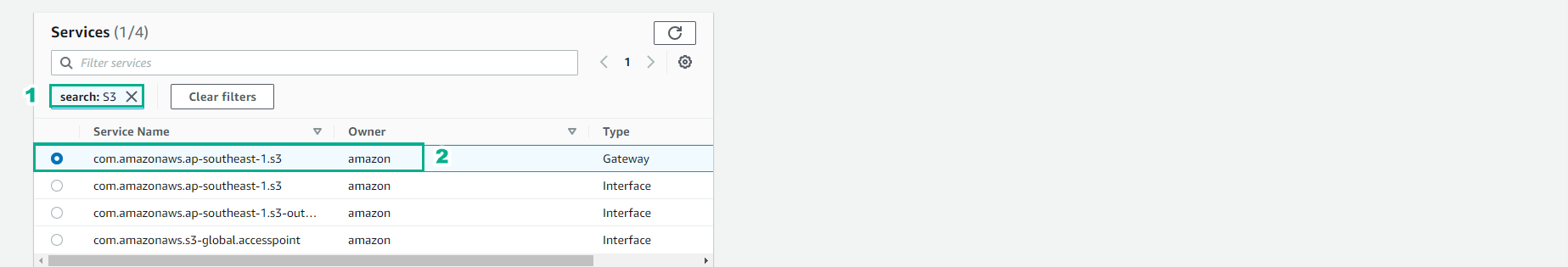
In services, we find S3
- Select Type Gateway
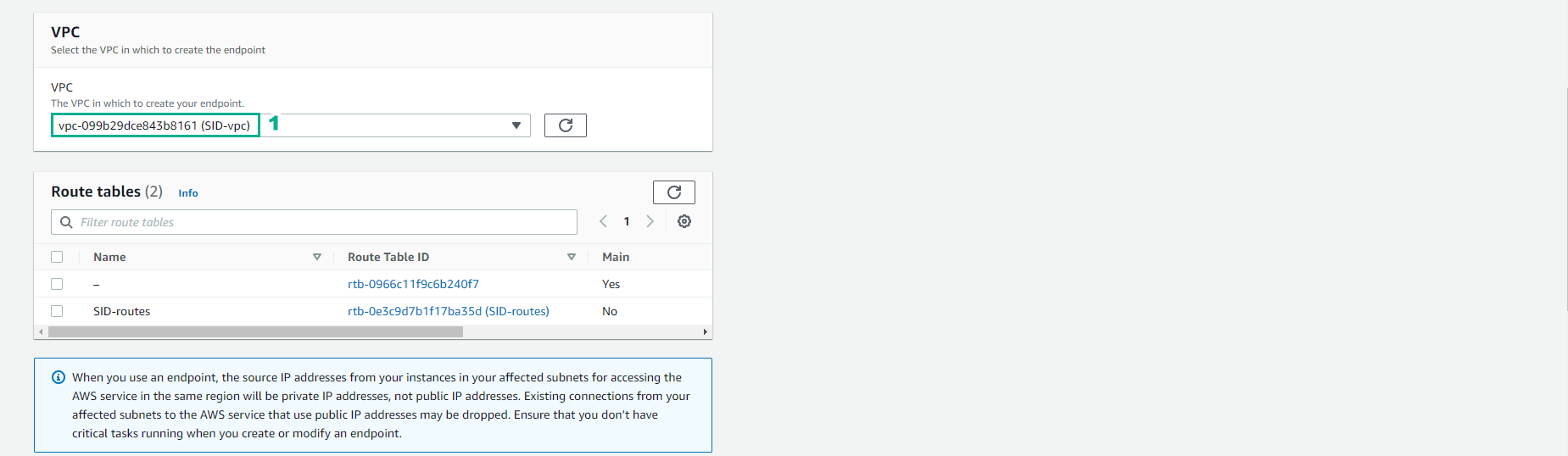
- Select VPC SID-vpc, do not select Route Table
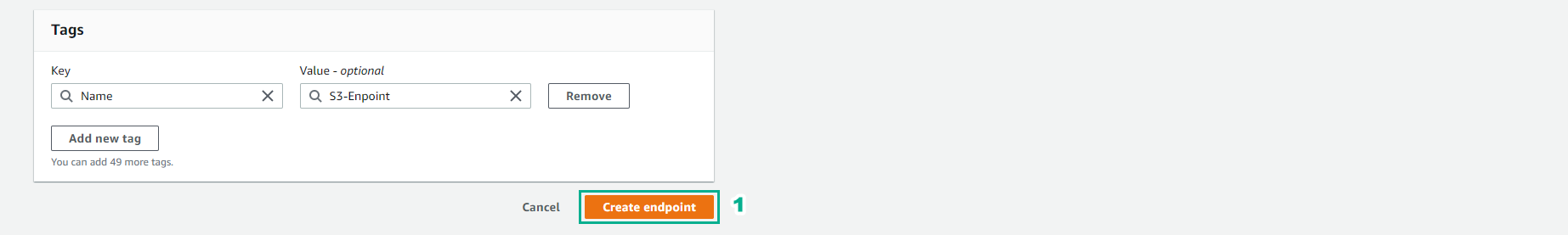
- Select Create endpoint
-
Successfully created VPC endpoint
- Note down Endpoint ID for the next steps
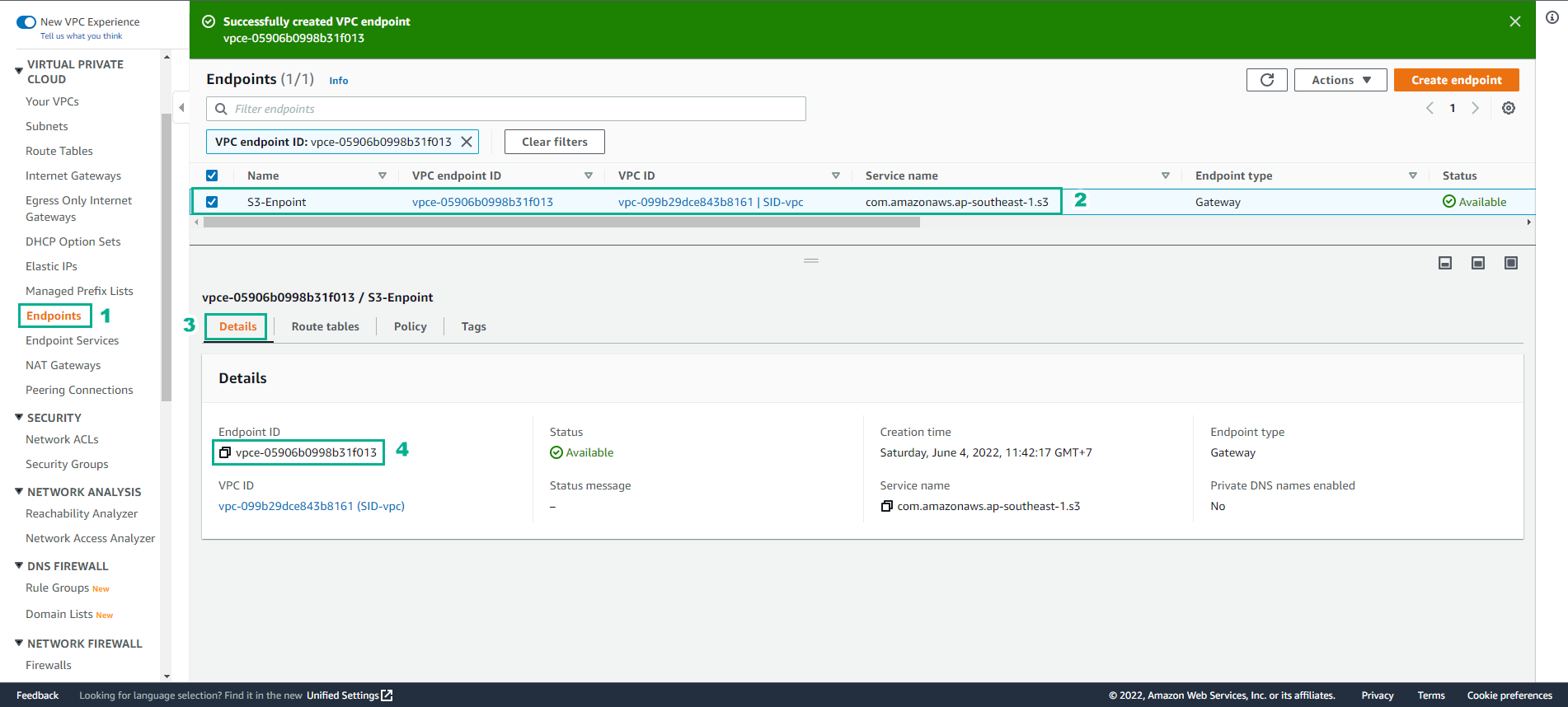
-
Access to S3 bucket
- Select sid-security-xxx bucket
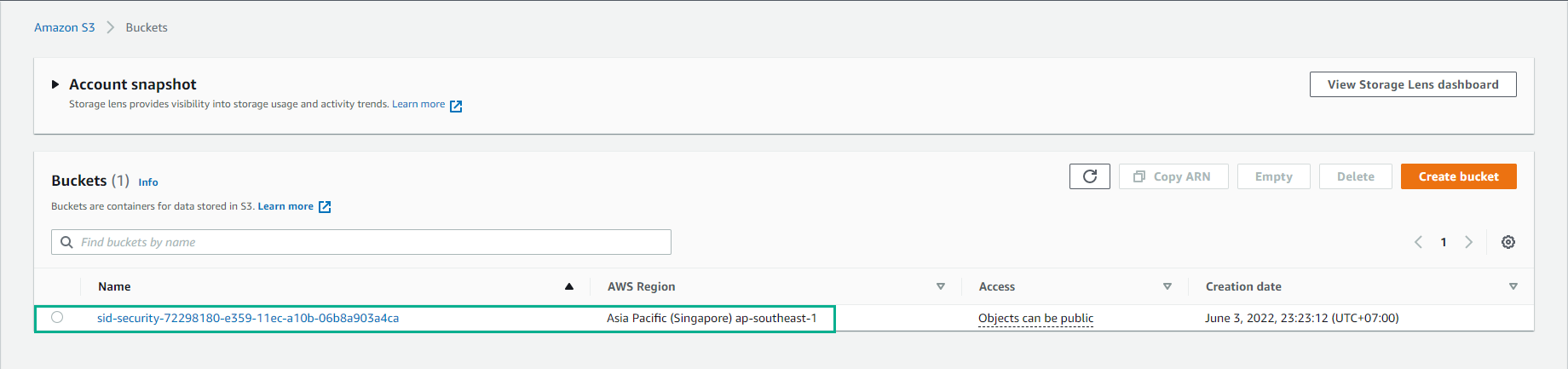
-
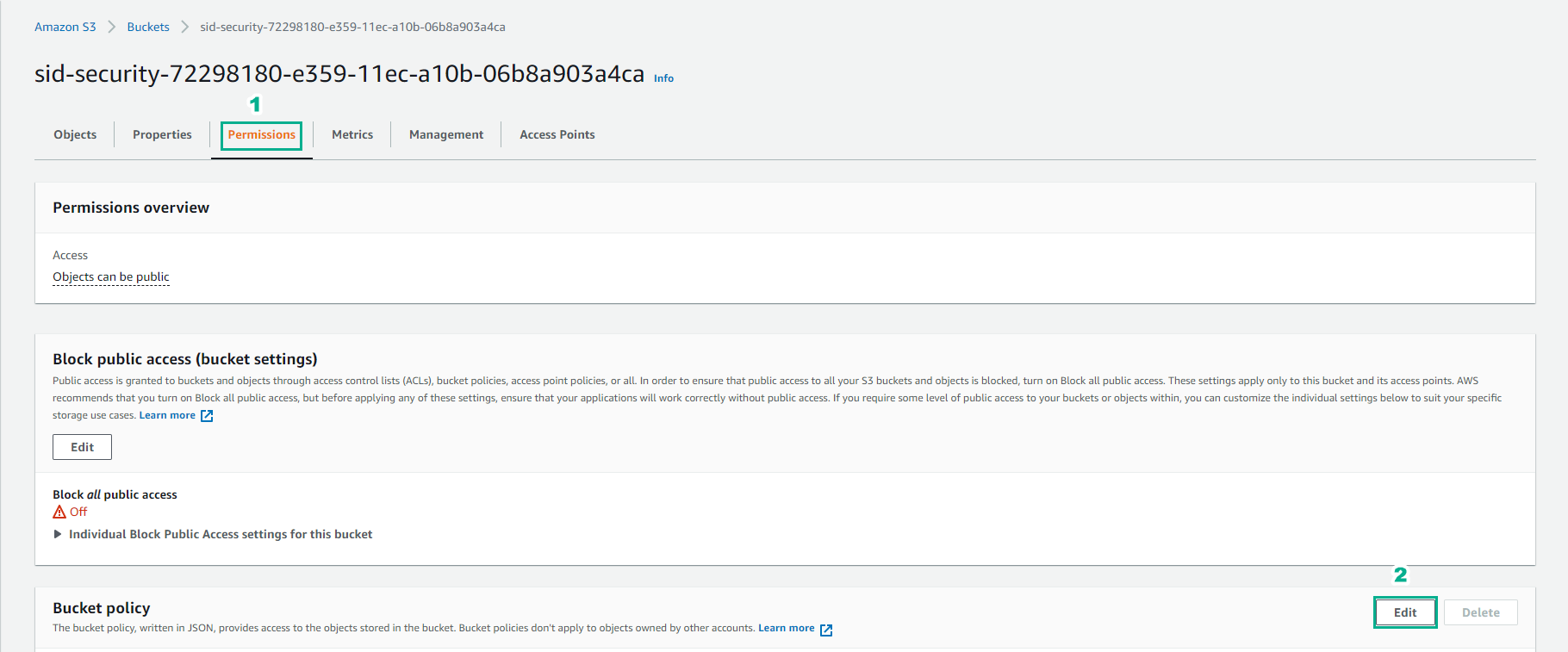
In the bucket interface
- Select Permissions
- Select Edit Bucket Policy.
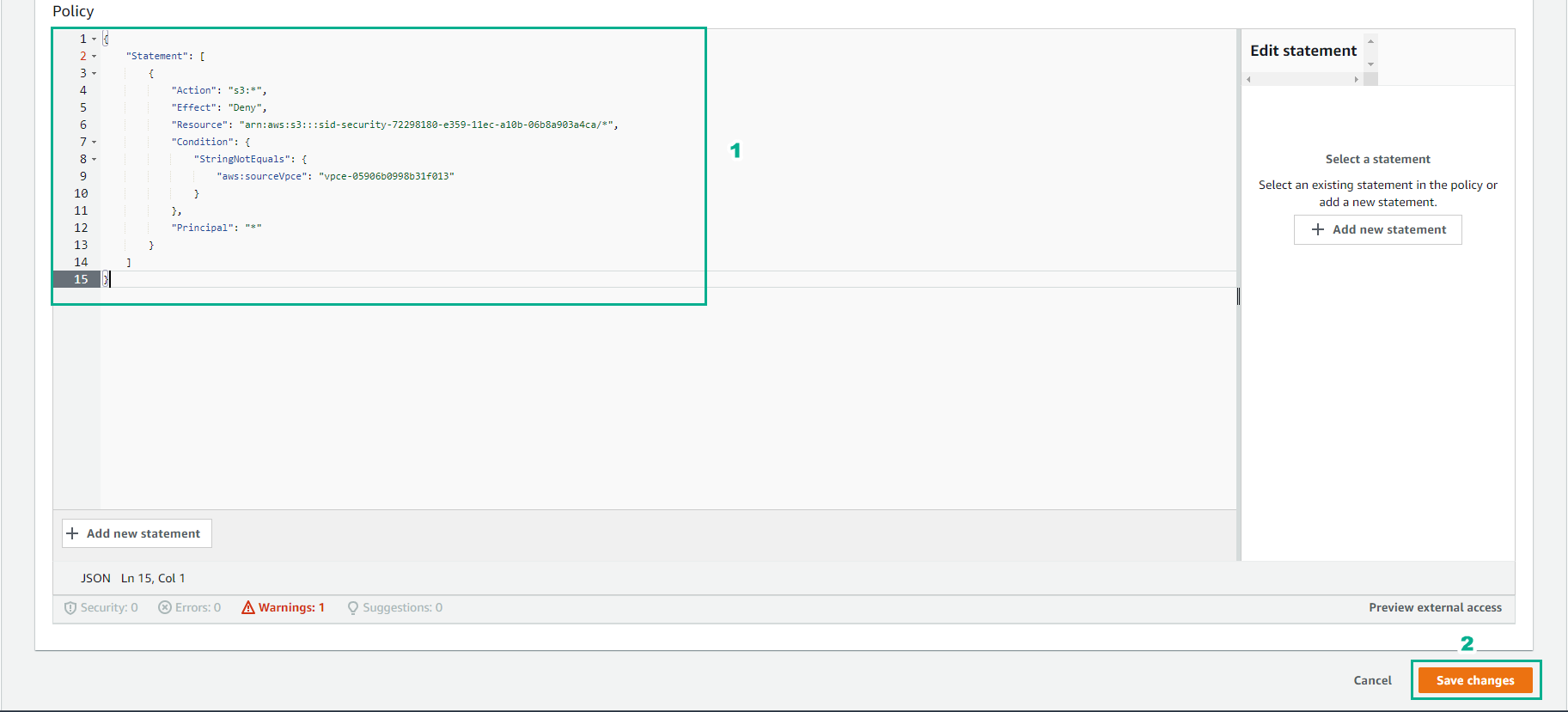
- Copy the bucket policy into the Bucket Policy Editor
{
"Statement": [
{
"Action": "s3:*",
"Effect": "Deny",
"Resource": "arn:aws:s3:::BUCKET_NAME/*",
"Condition": {
"StringNotEquals": {
"aws:sourceVpce": "VPC_ENDPOINT_ID"
}
},
"Principal": "*"
}
]
}
- Replace your **BUCKET NAME** and **VPC ENDPOINT ID**.
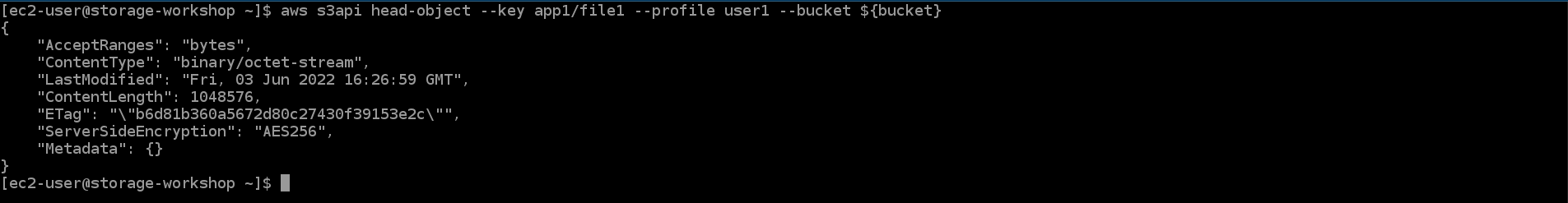
- Return to SSH interface
aws s3api head-object --key app1/file1 --profile user1 --bucket ${bucket}
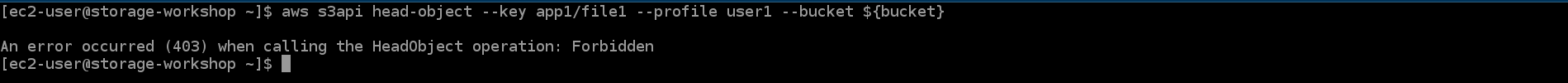
-
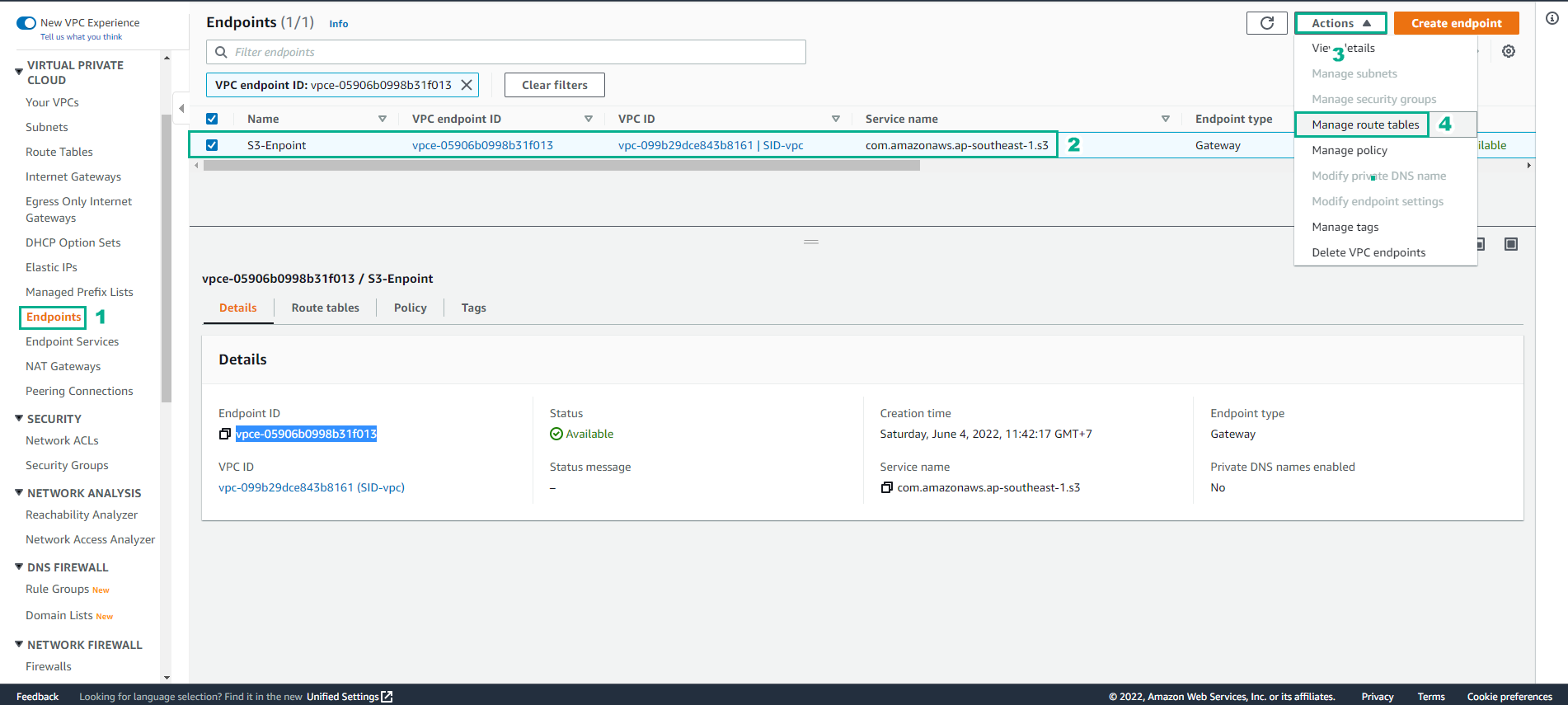
Return to VPC endpoint interface
- Select S3 endpoint
- Select Actions
- Select Manage route tables
-
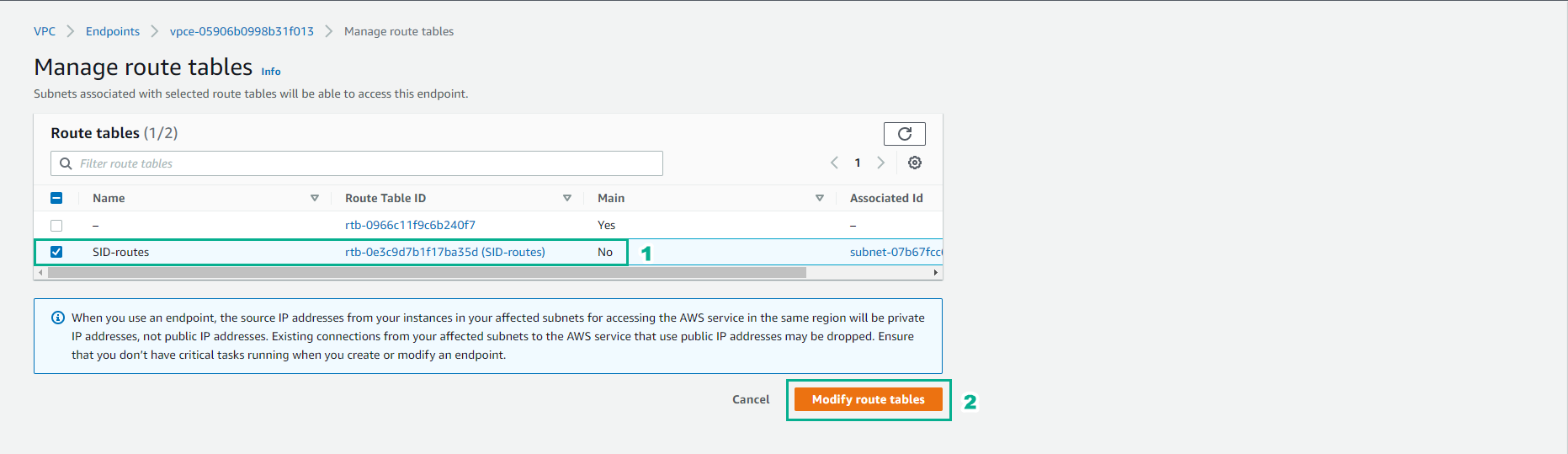
In the Manage route tables interface
- Select SID-routes
- Select Modify route tables
- Successfully added route table
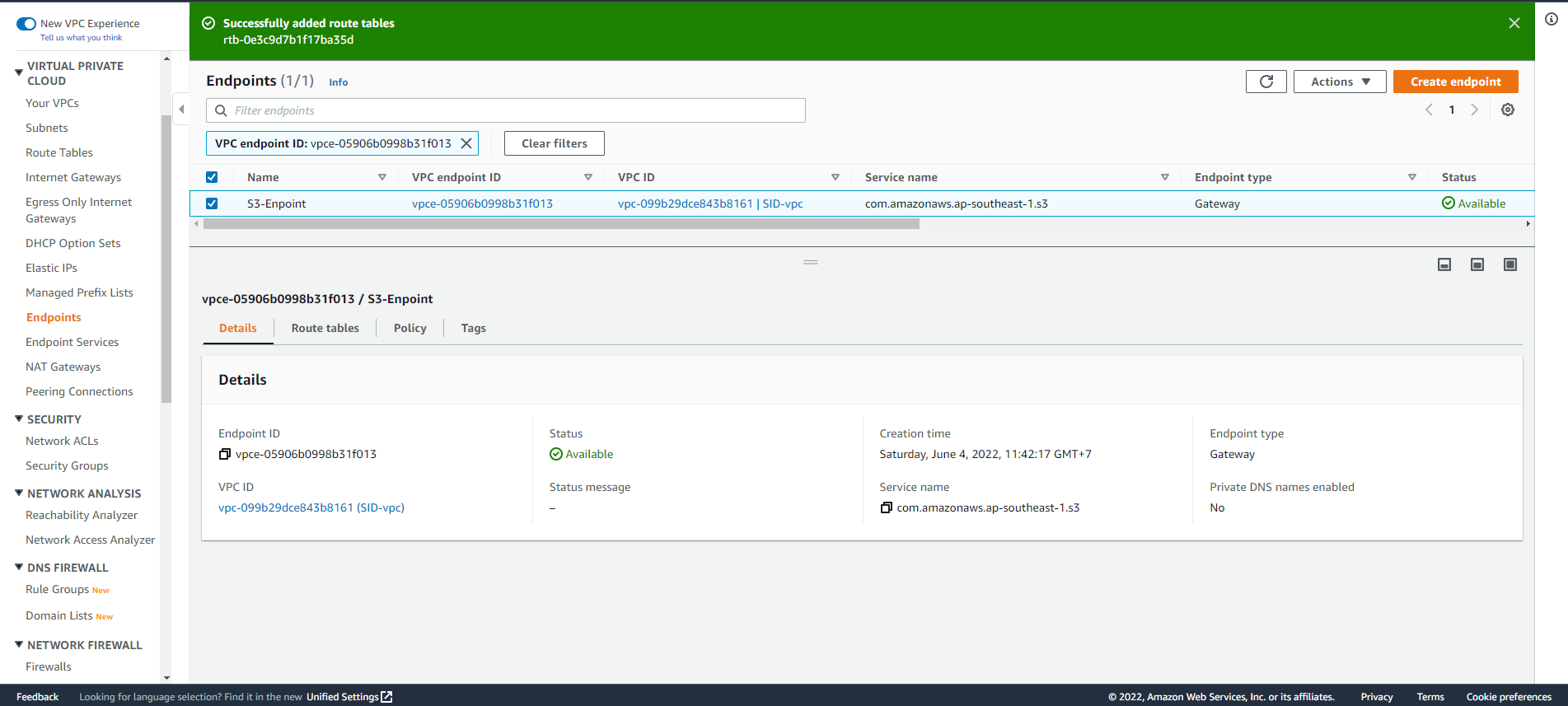
- Return to SSH interface
aws s3api head-object --key app1/file1 --profile user1 --bucket ${bucket}