Using AWS Config to Detect Public Bucket
Using AWS Config to Detect Public Bucket
-
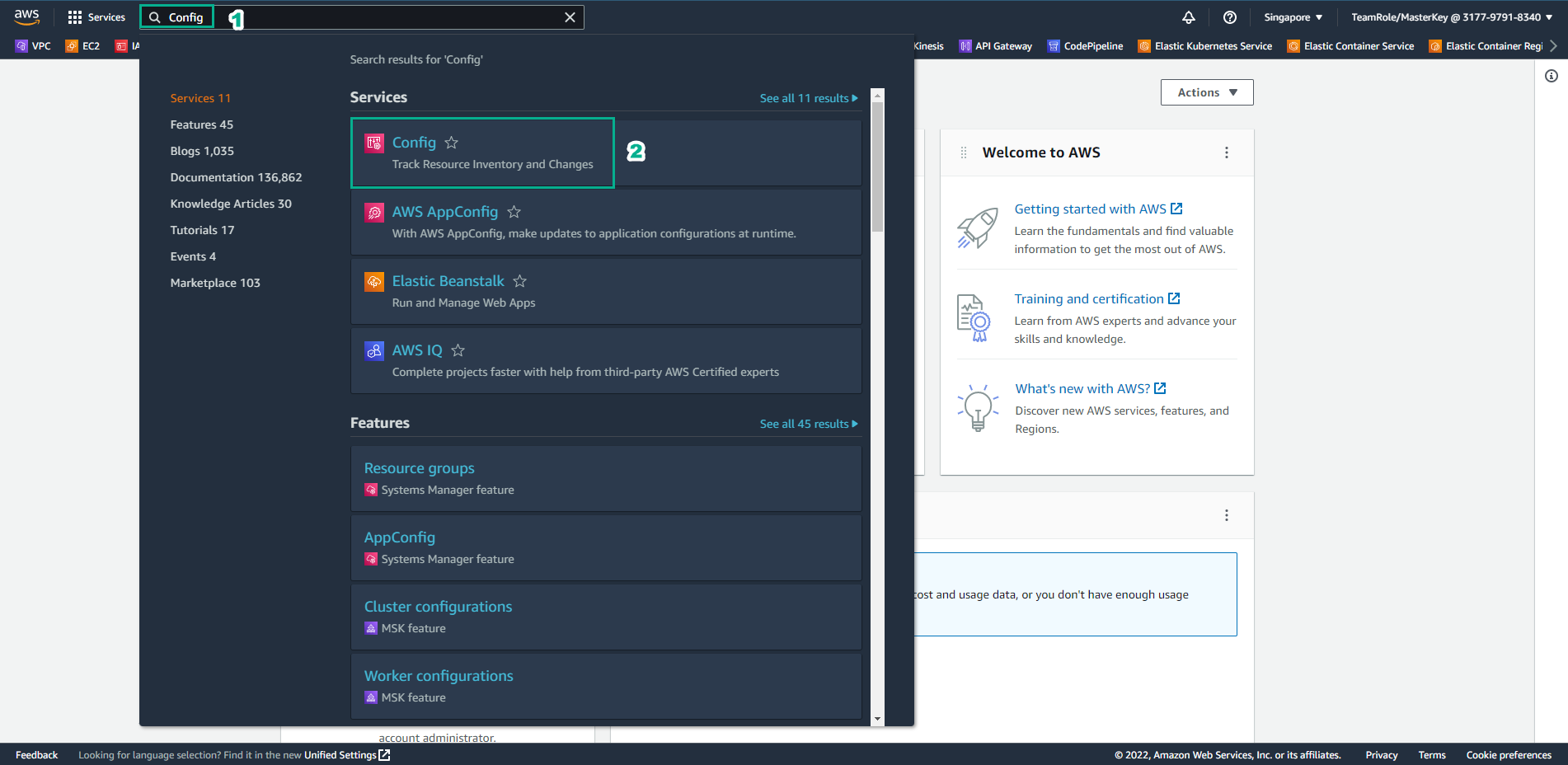
Go to AWS Management Console
- Find AWS Config
- Select AWS Config
-
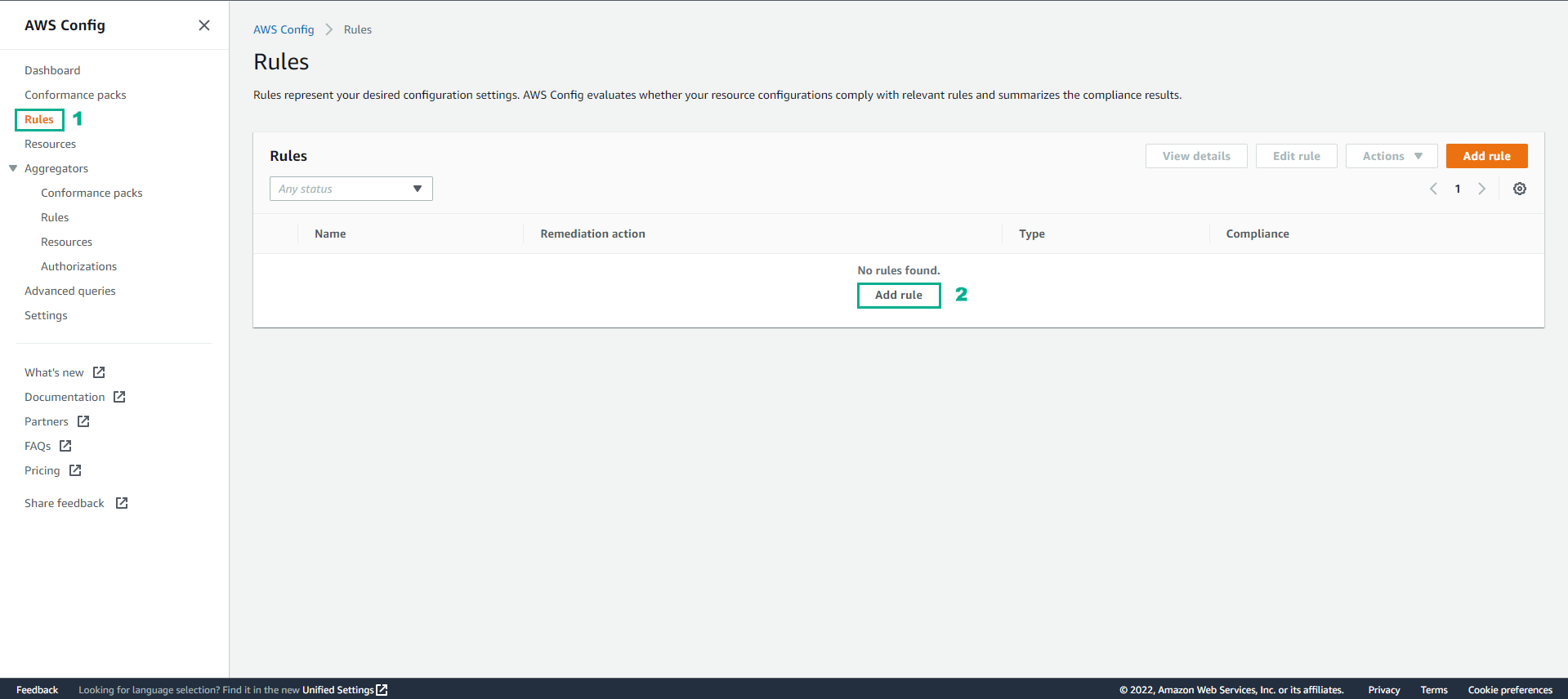
In the AWS Config interface
- Select Rules
- Select Add rules
-
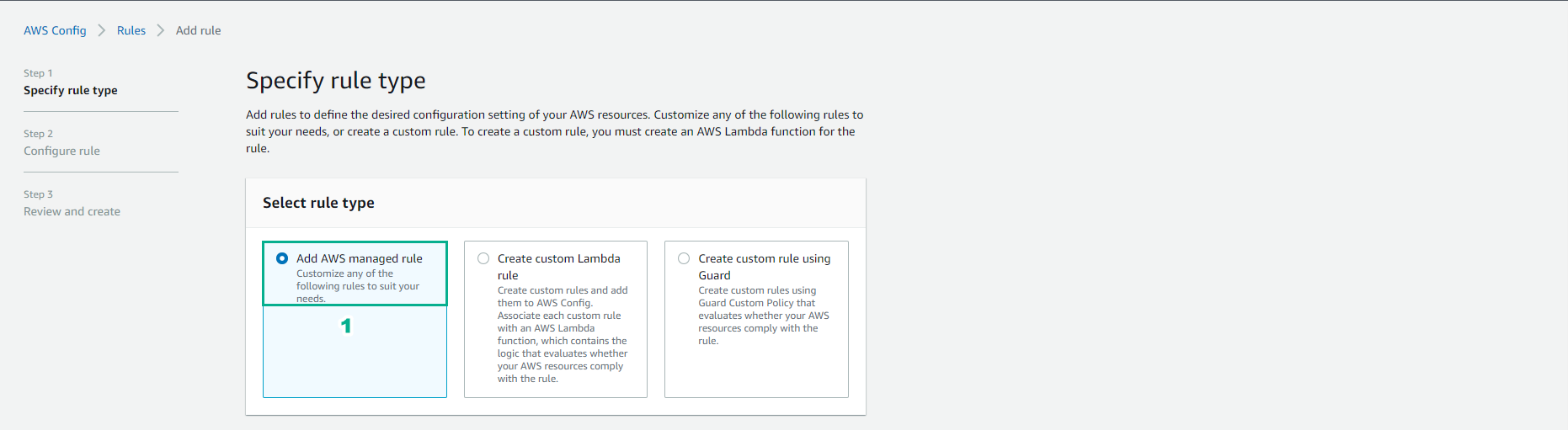
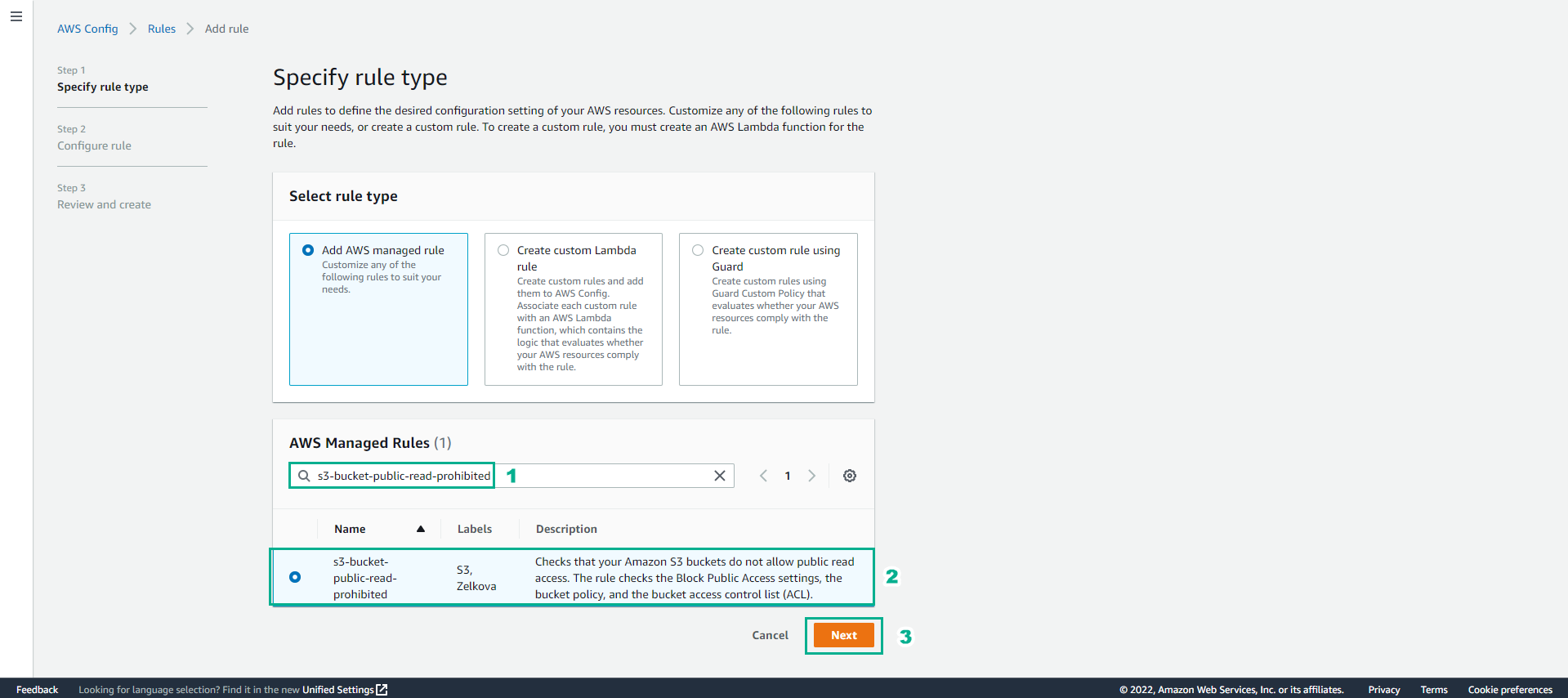
Choose a rule type
- Select Add AWS managed rule
-
For AWS Managed Rules
- Find s3-bucket-public-read-prohibited
- Select s3-bucket-public-read-prohibited
- Select Next
- Select Next
- Check again and select Add rule
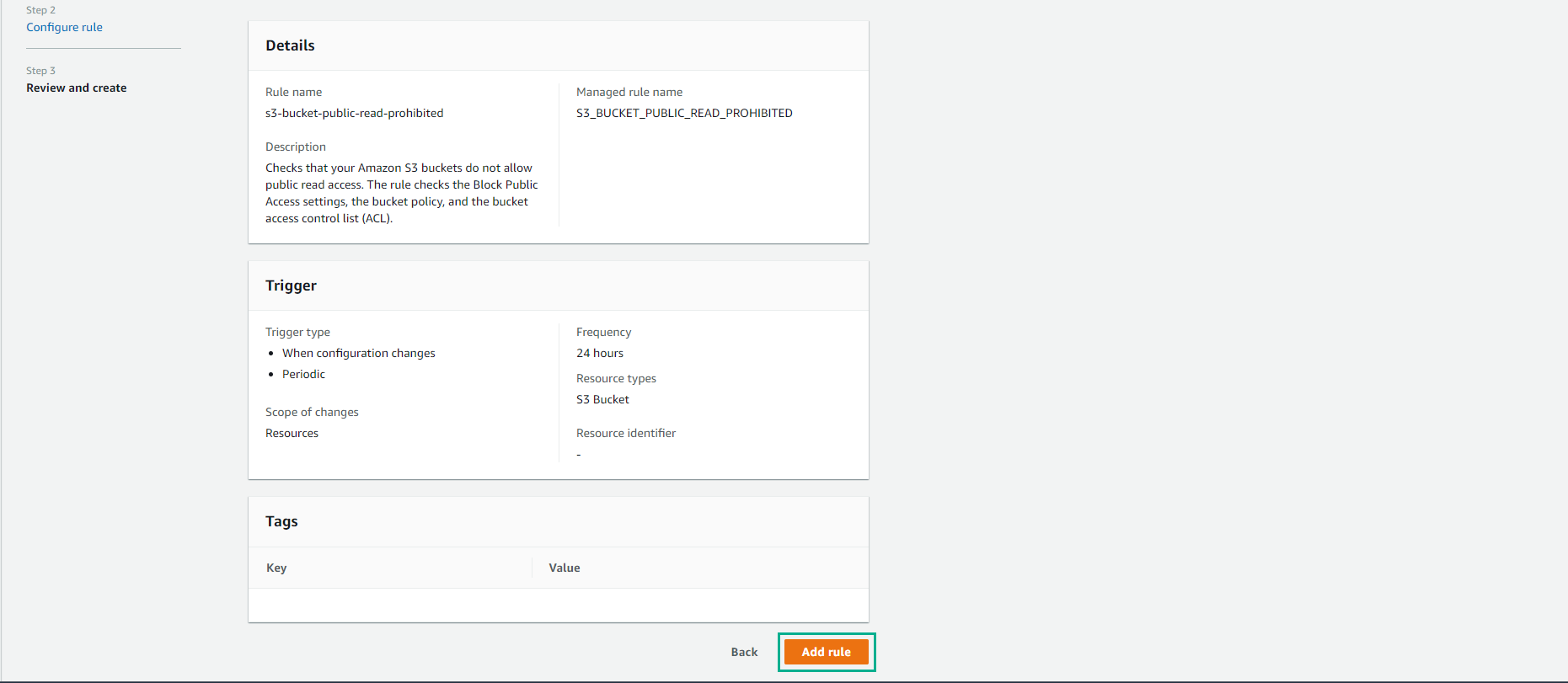
-
The rule has been added successfully.
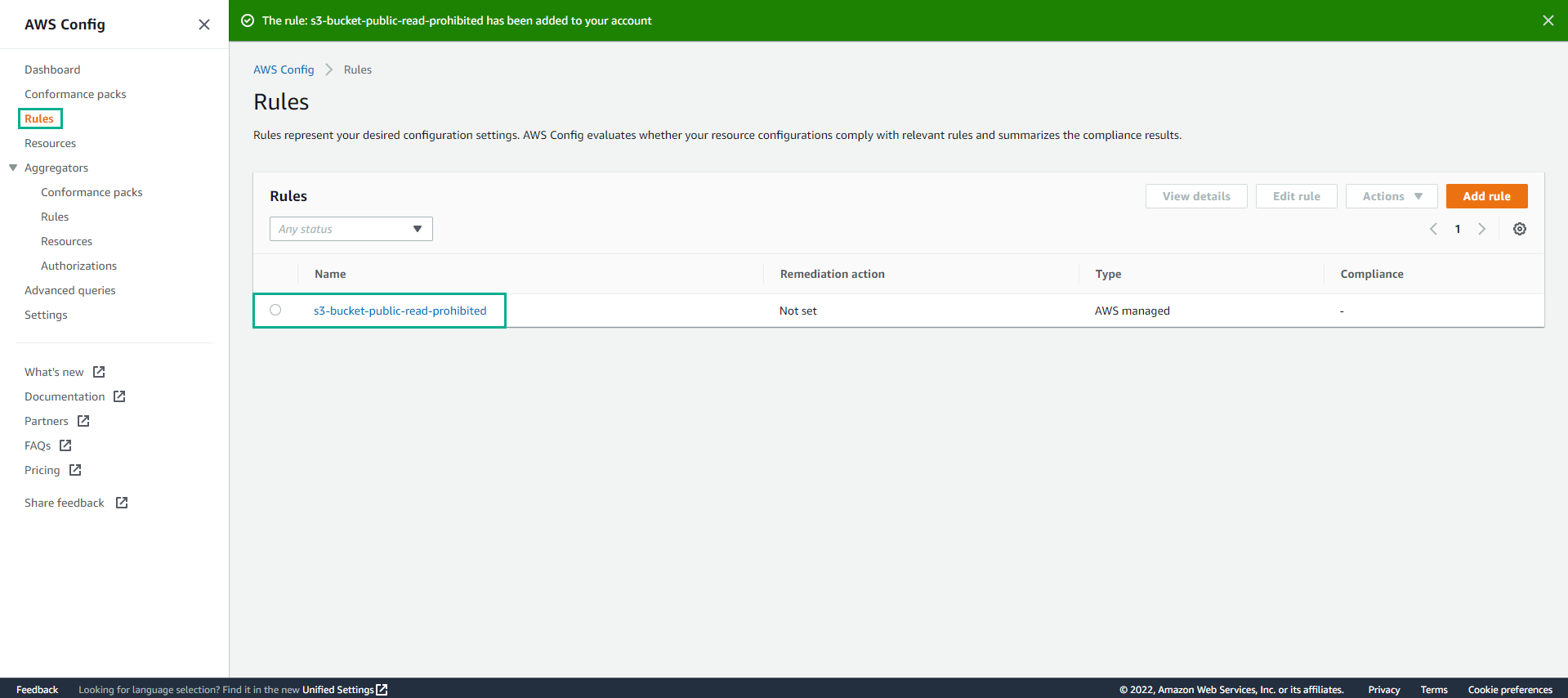
-
Go to AWS Config interface and select Dashboard
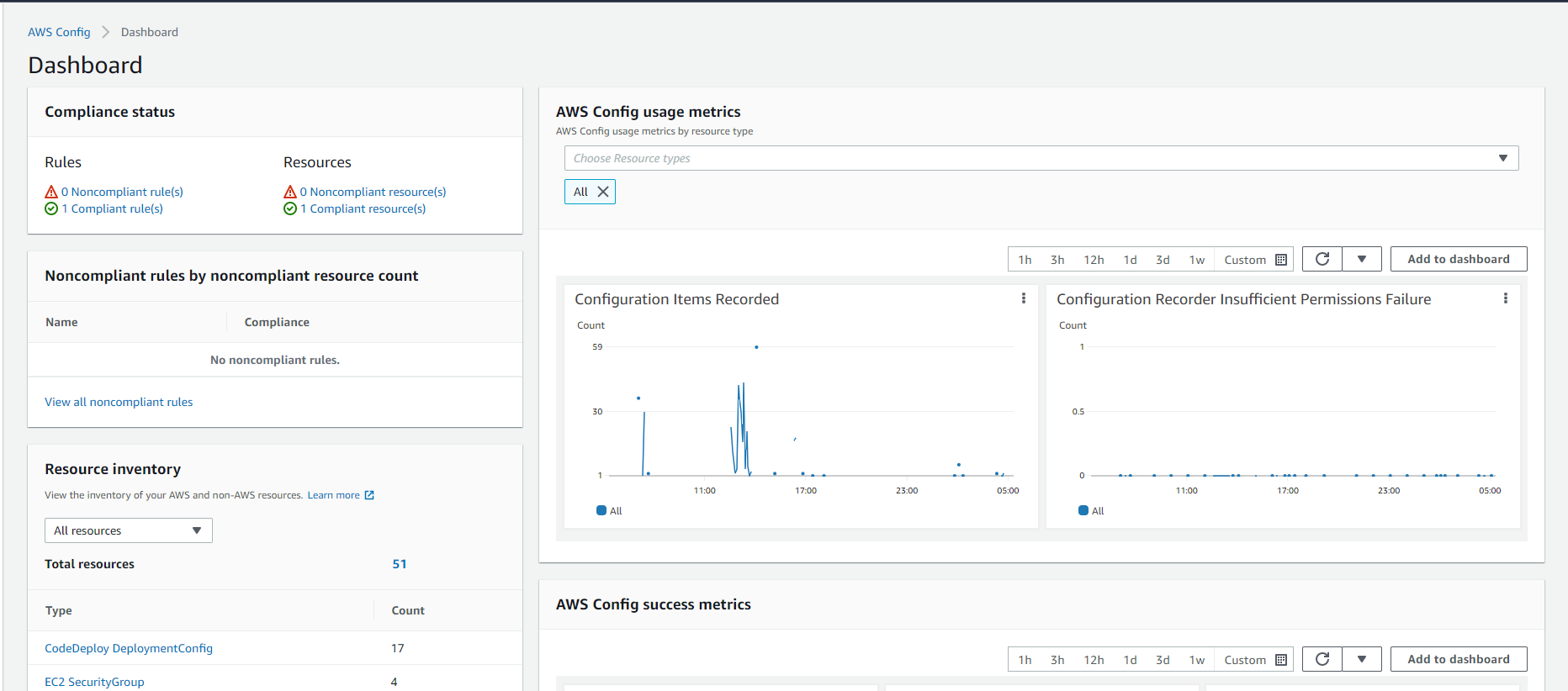
-
Return to S3 bucket interface
- Select sid-security-xxx bucket.
- In the bucket interface select Permissions
- For Access control list (ACL), select Edit
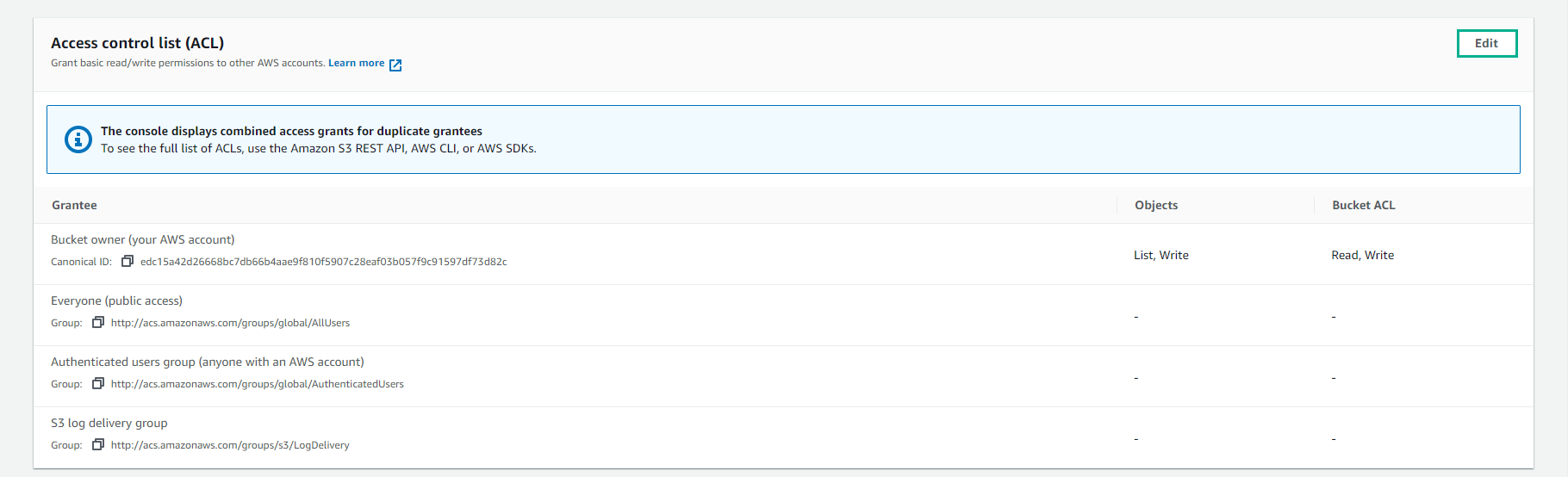
-
In the ACL editing interface
- For Everyone (public access), select List and Read
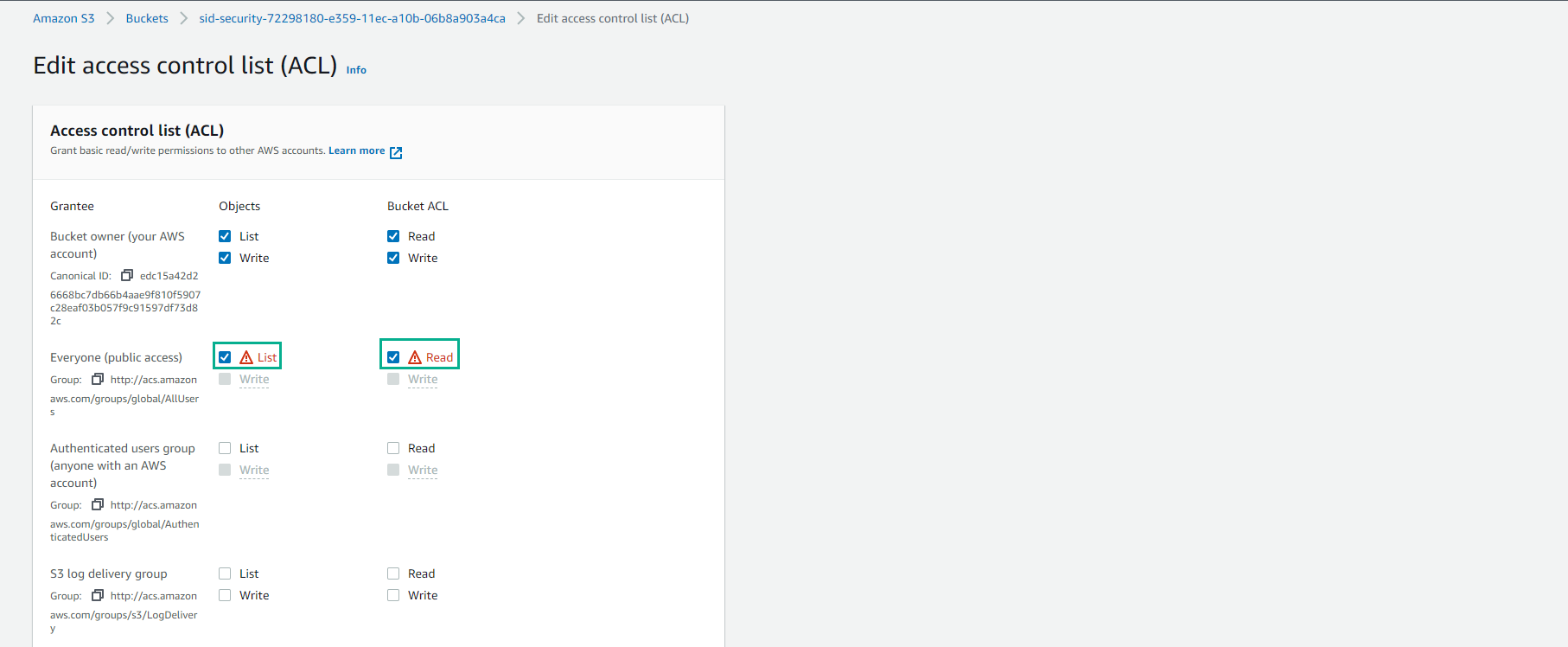
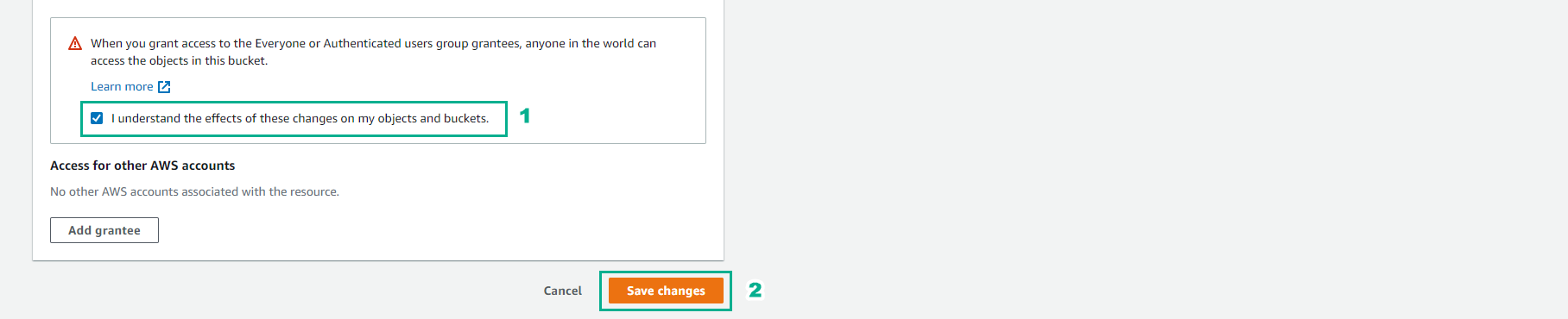
- Select I understand the effects…* and select Save changes
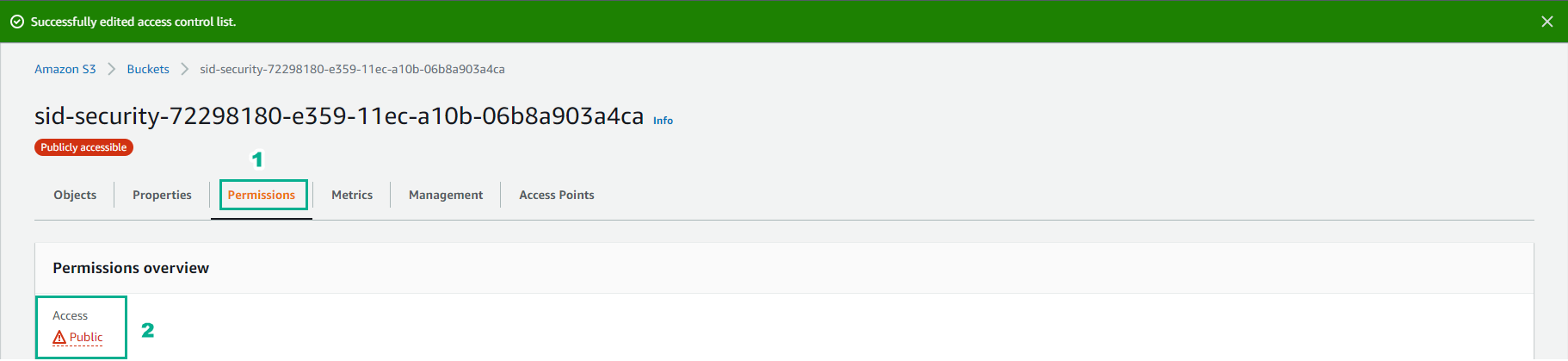
- Now we will see Permissions in state Public (Public Bucket)
-
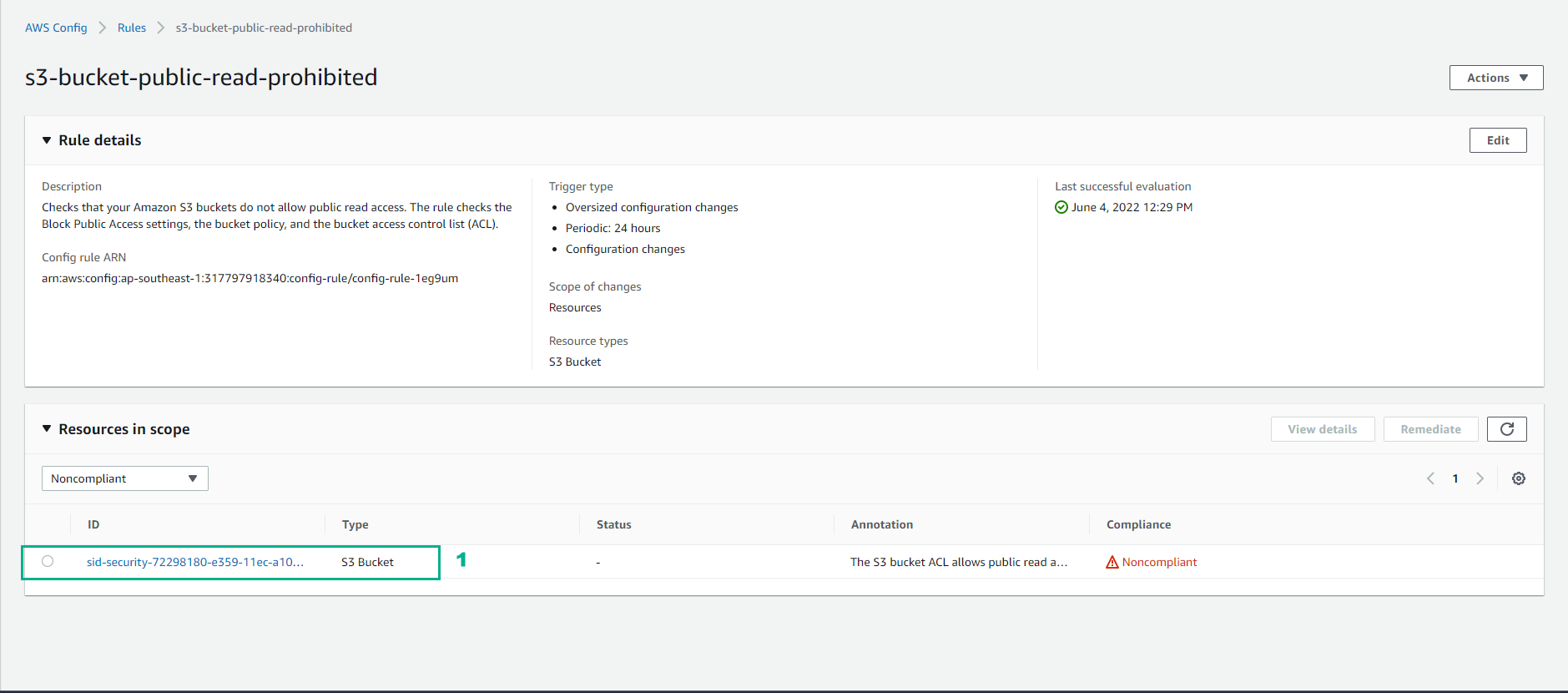
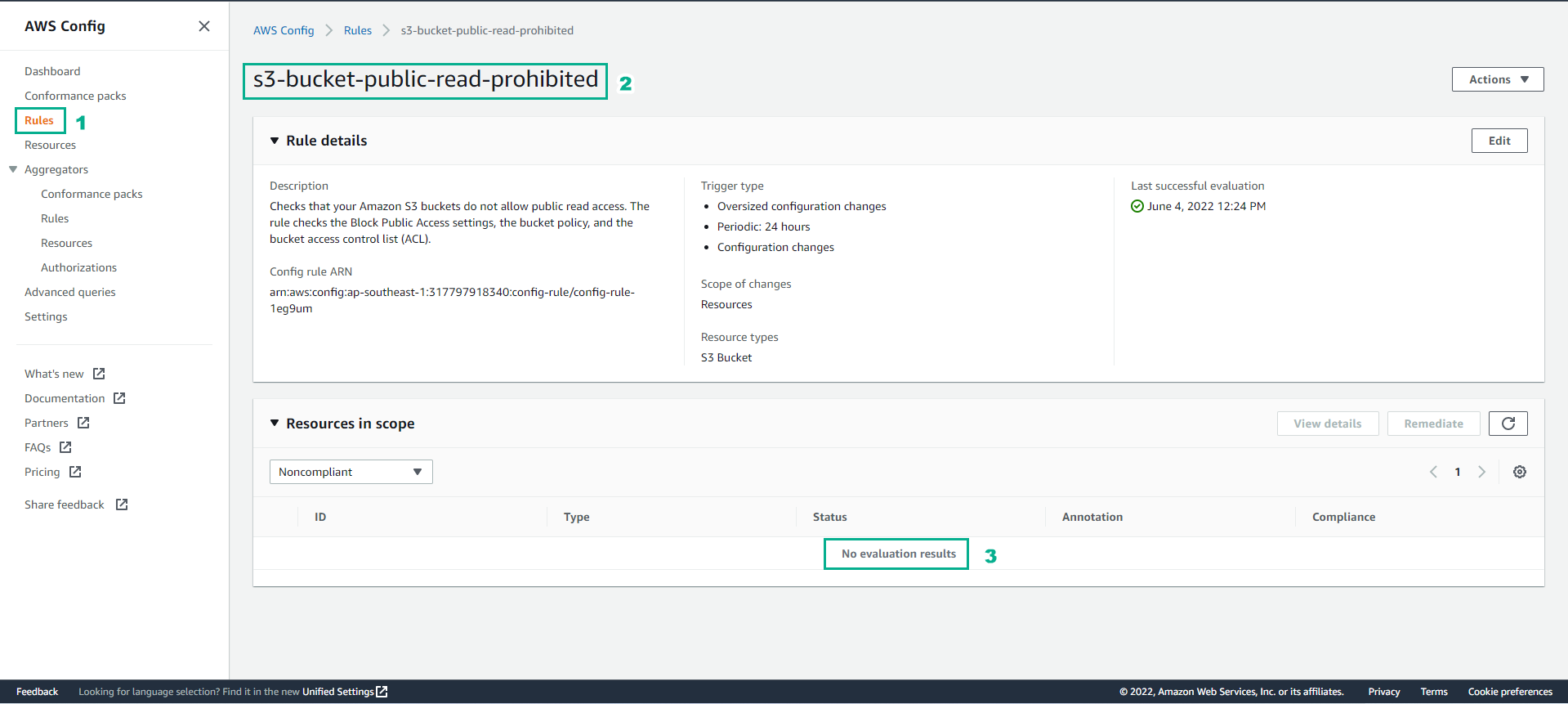
Return to Config interface
- Select Rules
- Select s3-bucket-public-read-prohibited
- Observation Resource in scope is currently not available.
-
In the same interface, select Actions
- Select Re-evaluate
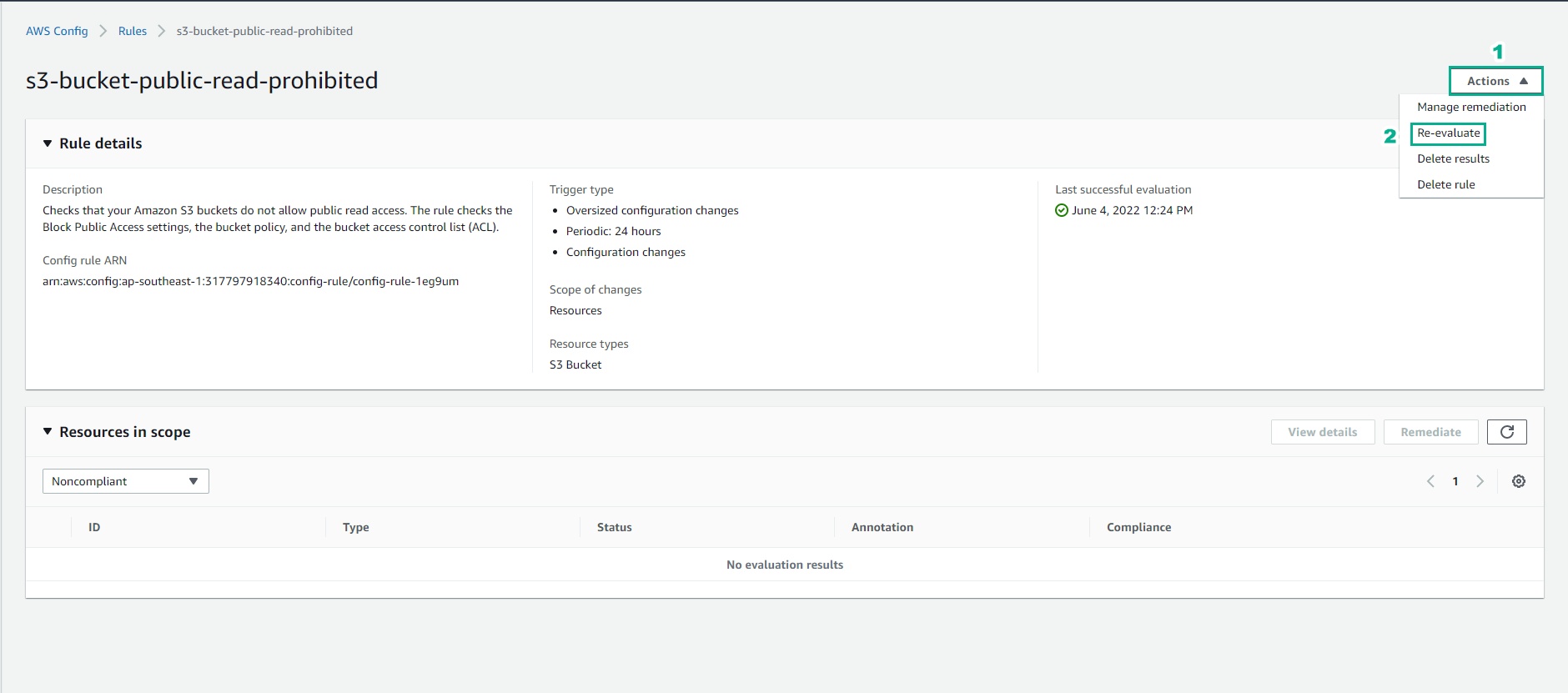
- Observe the Resource in scope section appears resource.